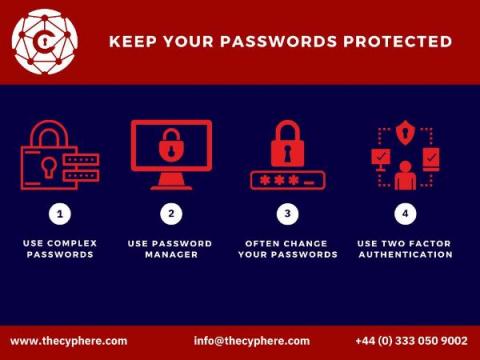
How can you Prevent Hacking? Tips to Protect Your Devices
With the rise in hacking and cyber-attacks, it is more important than ever to learn how to prevent hacking of your devices. No one wants their sensitive information or financial data get breached or their identities have taken over by a hacker. In this article, we will discuss tips and techniques for preventing hacking on your computer so you can be safe online.