DevOps Security Challenges and Best Practices
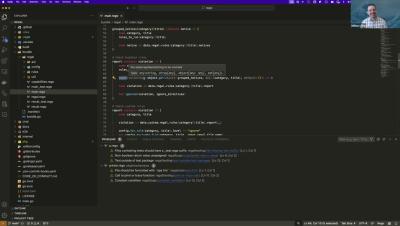
Some of the challenges when adopting DevOps security, also known as DevSecOps, are placing too much focus on tools rather than processes, cultural resistance, weak access controls and poor secrets management. While implementing DevOps security comes with its challenges, there are several best practices organizations can follow to make its implementation as effective and seamless as possible, including proper change management, combating secrets sprawl and following the principle of least privilege.