Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Panel Discussion: Cloud Security - Keeping Serverless Data Safe
Demystifying PCI Software Security Framework: All You Need to Know for Your AppSec Strategy
Whitesource and CircleCI Orbs: Secure your CI/CD Pipelines from Start to Finish
April Open Source Security Vulnerabilities Snapshot
Oh what a difference a month makes! When we launched our new monthly open source vulnerabilities snapshot series last month, we didn’t imagine that the following post would be researched and written by an unexpectedly remote team.
Surviving The Upside Down
If you were running a business that was not oriented to remote work, it has been completely turned upside down. Even if you were “remote-only”, it is likely going to be tough sledding for the foreseeable future given the resulting economic downturn.
Block Security Vulnerabilities from Entering Your Code
As continuous software deployments grow and become the accepted standard, security measures gain even more importance. From development and all the way through to production, security requirements should be adopted by all teams in an organization. JFrog IDE integrations provide security and compliance intelligence to the developer right from within their IDE.
Gravity: Run Cloud-Native Applications in Uncharted Territory
Gravity: Running Cloud Applications in Remote, Restricted and Regulated Environments.
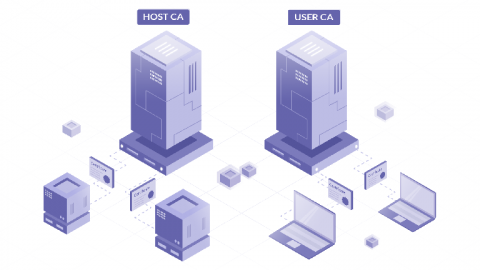
How to SSH Properly
There’s no denying that SSH is the de facto tool for *nix server administration. It’s far from perfect, but it was designed with security in mind and there’s been a huge amount of tooling written over the years to make it easier to use. In addition, many popular products and just about every server deployment system integrates with SSH somehow.