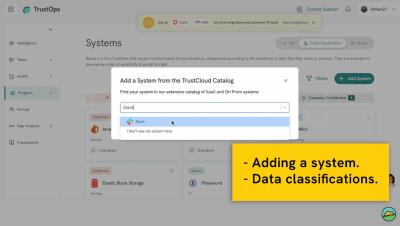
Understanding Zero Trust Network Access and Why Needs It
As flexible working arrangements become increasingly common across every industry, companies need secure, dependable ways to grant remote employees online access to company data, services, and applications. Productivity in today’s highly digital business environment depends upon employees being able to access the systems and information they need for work when needed, from any location.