Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Compliance
What Is A Compliance Management System?
Regardless of your industry, regulatory compliance is an important component of ongoing success. Staying on top of your compliance obligations can be challenging, and a strong compliance management program will require a compliance management system.
Securing the Supply Chain
A Beginner's Guide to Risk Mitigation and Management for Security and Compliance Professionals
Good data governance can go a long way toward reducing business risk. If your content and your data are secure, you’ve eliminated danger to your customers’ information and secured your proprietary information. From a digital perspective, you’re ahead of the game. But data governance shouldn’t be your only concern.
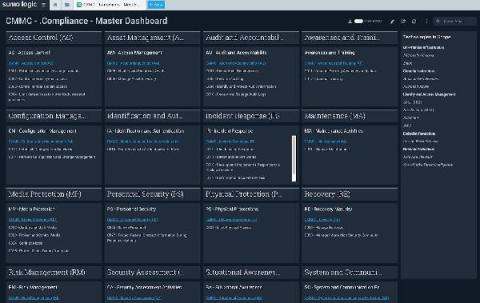
Cybersecurity Maturity Model Certification (CMMC): Tips for Compliance
Following a string of 83 data breaches in 2019 alone, the United States Department of Defense (DoD) established the Cybersecurity Maturity Model Certification (CMMC). The CMMC framework is a unified national standard for improving cybersecurity. Companies in the defense industrial base (DIB) must implement CMMC requirements in order to win contracts. Read on to find out how you can achieve compliance.
PHI Compliance: What It Is and How To Achieve It
For organizations that work in or partner with the healthcare industry, HIPAA compliance is of paramount importance. Keeping a patient’s medical records and personal information safe isn’t just a matter of avoiding penalties. It’s also key to building trust with patients and, ultimately, providing great patient care. Here’s what health organizations and their partners need to know about PHI and keeping it secure.
Is Zendesk HIPAA Compliant?
As an omni-channel customer service solution, Zendesk allows for companies to meet customers where they are by providing a variety of options for customer support, intake, and management of the overall customer experience (CX) process.
CMMC Compliance Made Easy with Sumo Logic
How to achieve MISRA and AUTOSAR coding compliance
Get practical steps for MISRA and AUTOSAR compliance to improve code quality, safety, and security in automotive software. Recent advancements in the automotive industry include the development of autonomous driving systems, connectivity units, and digital cockpits and infotainment systems that improve the user experience.
Announcing Synopsys as an OpenChain Project third-party certifier
Today, we are proud to announce the expansion of the partnership between Synopsys and the OpenChain project to include third-party certification. The OpenChain Project already recognizes the open source expertise of Synopsys in both the service provider and vendor space. This latest recognition ensures that Synopsys participates in and continuously aligns to the OpenChain Project and ISO/IEC 5230 compliance specification.