Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2022
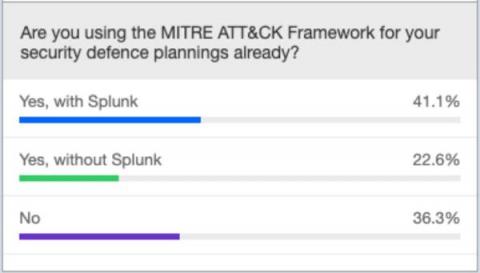
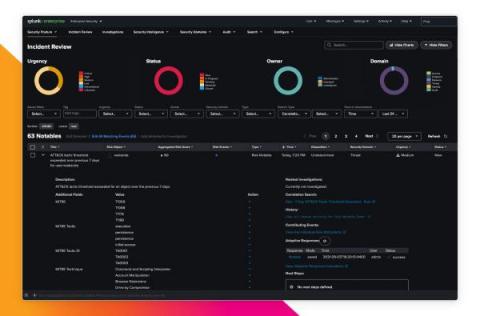
Answered: Your Most Burning Questions About Planning And Operationalizing MITRE ATT&CK
Hey There, Recently we ran a webinar ( English | German | French) in which we showed how Security Operations Teams can plan based on the MITRE ATT&CK Navigator, a threat-centric defense strategy. We also demonstrated how to operationalize it with content from the Splunk Security Essentials app via Splunk Enterprise Security. We received so many questions from attendees during the session that we weren’t able answer them all.
Coffee Talk with SURGe: 2022-APR-19 MS-RPC Vulnerability, Lazarus, Pipedream
The Upsurge in Ransomware Attacks in Australia and Opportunities to Protect Data
There are rare occasions when you open the news and don't find anything about cybersecurity in the headlines. According to the Australian Cyber Security Centre (ACSC), Australia has dealt with a cyberattack every 8 minutes in the financial year 2020-21, with over 67,500 cases of cybercrime registered in the same year. Studies indicate that ransomware is one of the most frequent and damaging types of malware leveraged by cybercriminals.
STRT-TA03 CPE - Destructive Software
The Splunk Threat Research Team is monitoring several malicious payloads targeting Customer Premise Equipment (CPE) devices. These are defined as devices that are at customer (Commercial, Residential) premises and that provide connectivity and services to the internet backbone. Examples include.
State of Security Research Details Essential Strategies for the Year Ahead
This year, security teams face more challenges — old and new — and grapple with high rates of burnout. Cloud complexity, supply chain attacks and additional obstacles are pushing security teams to the limits, and inspiring new responses. New research points to key strategies that will help organizations weather the complex challenges and attacks ahead.
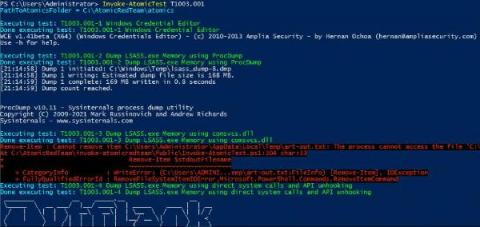
You Bet Your Lsass: Hunting LSASS Access
One of the most commonly used techniques is to dump credentials after gaining initial access. Adversaries will use one of many ways, but most commonly Mimikatz is used. Whether it be with PowerShell Invoke-Mimikatz, Cobalt Strike’s Mimikatz implementation, or a custom version. All of these methods have a commonality: targeting LSASS.
Coffee Talk with SURGe: 2022-APR-05 State Department, Elections, Spring4Shell, Certs/Lapsus$, RSA!
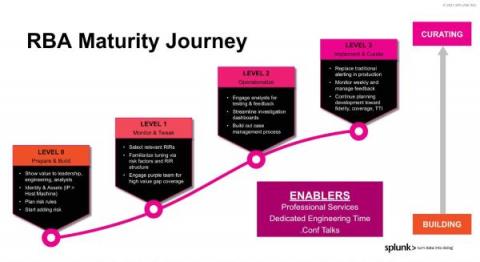
Risk-Based Alerting: The New Frontier for SIEM
If you haven't heard the gospel of risk-based alerting (RBA) in a SIEM context, by the end of this sermon you'll see why you’ll want it running in your environment yesterday, whether you're an analyst, an engineer, or in leadership.
Splunk Releases Add-On for Google Workspace Security Monitoring
As the trend toward having a more distributed labor force working remotely part or full time persists, Splunk continues to see strong customer demand for more visibility into the security of the productivity and collaborative products their employees use. To assist with these requests, we’re excited to announce the release of Splunk Add-On for Google Workspace 2.0. This second major release includes important changes requested by our customers and valuable new functionality.
Threat Update: CaddyWiper
As the conflict in Eastern Europe continues, the Splunk Threat Research Team (STRT) is constantly monitoring new developments, especially those related to destructive software. As we have showcased in previous releases in relation to destructive software and HermeticWiper, malicious actors modify their TTPs in order to become more effective and achieve their objectives.