Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2021
Why companies need URL filtering for enhanced cloud protection
The cloud landscape is rife with unsafe URLs and inappropriate content. This—coupled with the accelerated adoption of cloud applications in the workplace—has created an urgent need to scrutinize and control the use of these online resources to prevent data theft, exposure, and loss. This blog elaborates on how a robust URL filtering solution can help manage what cloud services your employees use and how they interact with these services.
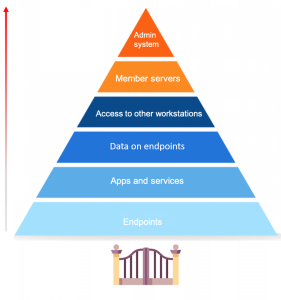
The role of endpoints in the security of your network
Endpoint security is a hot topic of discussion, especially now with so many businesses shifting to remote work. First, let’s define what endpoints are. Endpoints are end-user devices like desktops, laptops, and mobile devices. They serve as points of access to an enterprise network and create points of entry that function as gateways for malicious actors. Since end-user workstations make up a huge portion of endpoints, we’ll be focusing on their security.
The Colonial Pipeline ransomware attack: Lessons for cybersecurity teams
The recent ransomware attack on Colonial Pipeline is reportedly one of the most significant cyberattacks on the energy sector till date, and it has overwhelmed cybersecurity experts across the globe.
Five worthy reads: Confidential computing - The way forward in cloud security
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. In light of rising concerns over cloud cybersecurity, this week we explore the concept of confidential computing. The past year has seen strong adoption of cloud technologies due to accelerated digital transformation and a cloud-first approach in business.
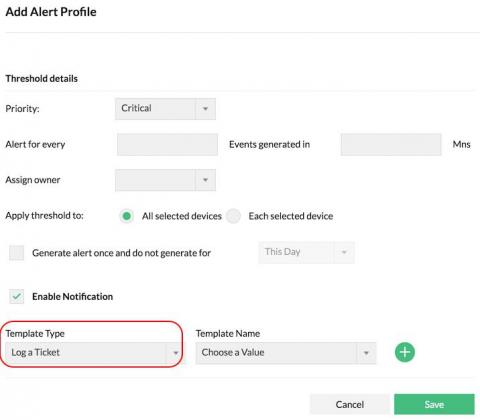
Resolve network security issues efficiently with the Firewall Analyzer-ServiceDesk Plus integration
ManageEngine Firewall Analyzer reviews firewall logs to capture network security threats. It generates alerts upon detecting security threats and attacks, and notifies you, the security administrator, in real time. You can configure alerts to be sent via email, SMS, and more. With these real-time notifications, you can troubleshoot to take instant remedial action. You can also make changes to your firewall policies and configurations to prevent recurring security incidents.
The importance of behavior analytics in your organization's cybersecurity
Collin’s dictionary defines “behavior pattern” as a recurrent way of acting by an individual or group toward a given object or in a given situation. Analyzing and understanding the behavior patterns of individuals has proven to provide in-depth solutions to problems in different walks of life, including cybersecurity.