Understand how Cyber Threat Intelligence can best leverage the capabilities of network detection and response
Intelligence is now considered essential to the process of identifying, understanding and acting upon threats. According to the “Global Perspectives on Threat Intelligence” study conducted by Mandiant, 96% of decision-makers interviewed for the research believe that it is important to understand which cyber threat actors could be targeting their organisation. Consequently, threat Intelligence should be fully integrated into the internal mechanisms linked to threat detection and response.
Before detailing how intelligence can be integrated into defense tools, it is necessary to talk about the nature of intelligence, the complexity of collecting it, and how to curate, qualify and act on it in the most efficient way. Intelligence effectiveness depends on the contextualisation of the elements collected in relation to a business’s specific environment. Once the qualified information is available and translated into specific formats and languages, it can then be used appropriately in detection tools, such as network detection probes, SIEMs, EDRs, etc.
In this article we will cover the utility, treatment, and cyber posture organisations can and should adopt to make the best use of CTI (Cyber Threat Intelligence).
Cyber Threat Intelligence Collection
In order to rely on qualitative intelligence, it is necessary to identify what information you are able to collect. To fully understand the different aspects of intelligence collection, we refer to three main approaches:
- Strategic intelligence: this helps you to understand what the actor is doing, who his targets are, which countries are his victims, which industries he is after, but also - and this is an important aspect – it enables you to learn the different threat actors aliases, other names they might use, and the relationship this threat actor has with others. The important thing here is not to rely on one trusted source but to diversify the sources to obtain the most relevant, cross-referenced intelligence, possible. Collecting intelligence from different sources (external, internal, OSINT, commercial) is key to having a complete intelligence base.
- Tactical intelligence: Relying on the MITRE ATT&CK® matrix, for example, will allow you to learn the techniques used by a given actor. Nevertheless, the knowledge of TTPs (Tactics, Techniques and Procedures) is no longer sufficient. It is essential to understand and know the sub-techniques involved in the various attacks. This is the operational part of CTI that will be particularly useful for security teams.
- Technical intelligence: This is the technical data: IoC (Indicators of Compromise), signatures, etc. that allow us to identify suspicious activity. This information will allow us to technically identify the presence of elements potentially linked to an adversary.
Threat Intelligence Qualification & Normalisation is essential
When intelligence is collected from multiple sources and centralised in a Threat Intelligence Platform (TIP), it is essential to qualify and normalise the data in to a single format to make it relevant, intelligible, and actionable in a specific context. According to customer feedback, only about 10 to 15% of all the intelligence collected is relevant in a defense strategy for any given client. All intelligence feed providers have their own scoring mechanisms, which are the same regardless of the customer’s context. It is therefore necessary to qualify these scoring mechanisms by weighting them based on what is really important in the specific customer’s context.
Capturing Value from Cyber Threat Intelligence
Threat Intelligence has become a fundamental ally for threat anticipation, detection, analysis and response. It allows organisations to better understand who could target them, why, but also how. Then it is possible to identify relevant threats and adopt an adequate posture toward them. For example, it will be possible to follow a group of actors; to identify if a malware is potentially present in their infrastructure, or to verify the presence of an IoC. Threat intelligence helps security teams to collaborate on threats, make the link between the different perimeters, and take the appropriate decisions in response to a threat situation.
With personalised intelligence and a detailed understanding of the different actors who can target the assets of their customers, organisations can now monitor and structure the intelligence and utilise it. A TIP is highly valuable to achieve this.
Importance of a Threat Intelligence Platform
Originally, a threat intelligence platform was simply used to collect intelligence on threats. Today, a TIP is a tool that sits at the heart of a business’s defense strategy. It is integrated into a technical ecosystem, and it is also adapted to the processes that are in place. Its role has evolved and expanded.
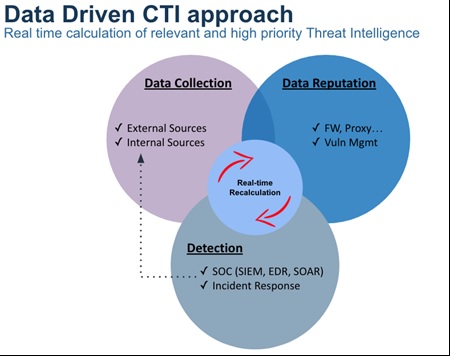
The TIP’s role is to reconcile different elements of the threat intelligence world, such as:
- The collection of several sources, both external and internal.
- The reconciliation of data reputation in the customer context, so all the issues relate to the protection of customer’s critical assets.
- The correlation between detectiontools, with the elements that come from SIEM, EDR, NDR, orchestration, but also the work done by incident response teams. It is truly representative of what is happening in a client environment.
Everything that comes from the last perimeter (the detection phase) is essential in the client context, as it will reflect the reality of what is actually happening on their network, and this information does not lie.
The role of the TIP is therefore to be able to ingest, normalise, correlate, prioritise, translate and orchestrate the information, recalculating each time new data is collected, with the aim of anticipating future threats.
ThreatQuotient’s vision of the reconciliation of different perimeters of the threat intelligence world
Feeding detection tools with Cyber Threat Intelligence
One of the benefits of having intelligence is the ability to exploit it for operational security purposes. Indeed, with the help of well-described processes, it is possible to capitalise on the intelligence collected (external or internal) and to feed the different detection tools with qualified intelligence.
On the other hand, one of the SOC’s (Security Operation Center) challenges - especially in the world of detection - is to fight against alert fatigue and to limit false positives. Transferring raw intelligence into detection tools is not necessarily efficient insofar as this intelligence is not "contextualised" in relation to a given environment, nor is it in the format or language that individual tools use. The risk of false positives is therefore increased and the attractiveness of the intelligence to the analysts in charge of security alerts may therefore be reduced.
It is thus necessary to have a TIP that will be able to “translate” and “orchestrate" all the intelligence, make it intelligible, qualified, and then usable by the various detection tools. It is preferable to send only high priority and relevant intelligence to the devices. Focusing on the top 15% of the relevant intelligence for the organisation will result in contextualised alerts rather than sending everything to the tools and ending up with hundreds of unqualified, irrelevant alerts. In this architecture, the TIP plays the role of orchestrator by classifying threat intelligence and distributing it to the right places according to the different perimeters, issues, and needs.
Conclusion
Nowadays, threat intelligence is a necessary pillar of defensive cyber strategy. It must be at the heart of the tooling strategy, and especially at the center of the various processes set up by organisations to monitor and defend their environment. The collection, standardisation, structuring, and dissemination of CTI are all elements that can allow companies to protect themselves from threats by adopting a proactive posture.
Threat Intelligence Platforms such as ThreatQuotient provide automation capabilities to orchestrate intelligence in order to help teams optimise their time, but also to help them constantly reevaluate what is important in their context and therefore, to be able to update their defense strategy very quickly.
A TIP, associated with contextualised CTI and a clear strategy to prioritise the threat data collected are key elements that security operation teams and decision-makers need to rely on to be able to adopt an effective proactive posture.
