The Importance of Security in Web Development
Today, internet applications have a significant share of performing tasks in different spheres of life—both commercial and personal ones. Today, the use of web technologies has gone high, thereby invoking extra measures to protect these technologies and platforms. Security cannot be overemphasized in web development since emerging vulnerabilities mean great losses—reputation loss, given the rapid expansion of internet users in the universe, as well as millions of dollars.
The Consequences of a Breach
That is why it becomes mandatory to increase the level of security of web applications. The potential consequences of the violation of web application security are catastrophic. The financial costs are usually quickly noticed in the company, but the damage to reputation and user loyalty may take a long time to heal. According to IBM’s “Global Cost of a Data Breach Report 2023,” for instance, the global average cost of a data breach is $4.45 million and is rising. This figure just includes the tangible cash lost from fines and any disruption in revenue, but does not include the intangible value or the shaking of reputation, which would take years to regain.
Some of the statements found include, “Security is not a product but a process.”
— Bruce Schneier, Cryptography and Computer Security.
Take the Equifax breach in 2017 as an example of a firm where information about 147 million people was exposed. The company is still facing many related legal issues and has incurred direct costs of more than 1.4 billion U.S. dollars. However, not only large corporations are likely to feel the pinch. SMEs are considered less secure targets for cybercriminals, and about 60% of small businesses do not survive more than six months after being attacked.
The consequences are not limited to the pluses on balance, although... A compromised system may result in identity theft, unauthorized access to secret information, and theft of idea property. In addition to that, failure to ensure user data privacy results in companies being on the wrong side of the law, and they will also end up lagging behind in the market. Status and trust, once lost, are very hard, if not impossible, to come back despite the many efforts made by various organizations.
Common Security Threats
No less than numerous security threats pose a risk to web applications, and it is crucial to study them to forestall them. The most commonly used threats are SQL injections, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), Distributed Denial of Service (DDoS) attacks, brute force attacks, and software misconfiguration.
SQL Injections (SQLi)
In fact, up-to-date SQL injection has been cited as one of the most severe threats to web applications. This type is achieved when the attacker manages to input an undesirable SQL code into the database, then the attacker can get full permissions to more data or even delete all the databases. SQL injection can be disastrous; an example of a SQL injection attack happened at TalkTalk in 2015 when hackers, through SQL injection, compromised 156,000 customers’ details.
SQL injection attacks are common and predominant because many web applications fail to validate user input or sanitize the inputs used in queries. To prevent such attacks, the website should use parameterized queries where parameters are only values and not commands.
Cross-Site Scripting (XSS)
Other common threats which refer to attacking user browsers are Cross-Site Scripting (XSS). XSS happens when a malicious person injects Web content with scripts that will be executed by other users. These scripts can then perform unauthorized actions such as Hijack session cookies, capture keyboard strokes, as well as take the user to desired sites.
Such an attack is especially hazardous for sites that store or process customers’ data, such as accounts from shopping online services or social networks. To avoid cross-site scripting, the application's inputs have to be validated and encoded so that scripts cannot be run on them.
Cross-Site Request Forgery (CSRF)
CSRF attacks take advantage of the fact that a website has to rely on the client side of things. In this type of attack, an attacker contrives a way to get the victim to make a request on a web application that the victim is logged in to without the victim's knowledge and consent. For example, a legitimate user is online, and an attacker could impersonate himself and capture details from the logged-in victim and offer to transfer a certain amount of money or change some account credentials.
In order to prevent CSRF attacks, one must use anti-CSRF tokens, which would help assure every request by a user is authentic. They are usually placed in forms and checked on the server after receipt of requests to confirm that they are real.
Distributed Denial of Service (DDoS)
DDoS intends to overload the web server with a massive traffic rate beyond the limit all permitted users can access the service. Although DDoS attacks do not threaten the data in any way, they can result in a great deal of system unavailability and affect commercial operations. What can make a business lose money and harm its image???
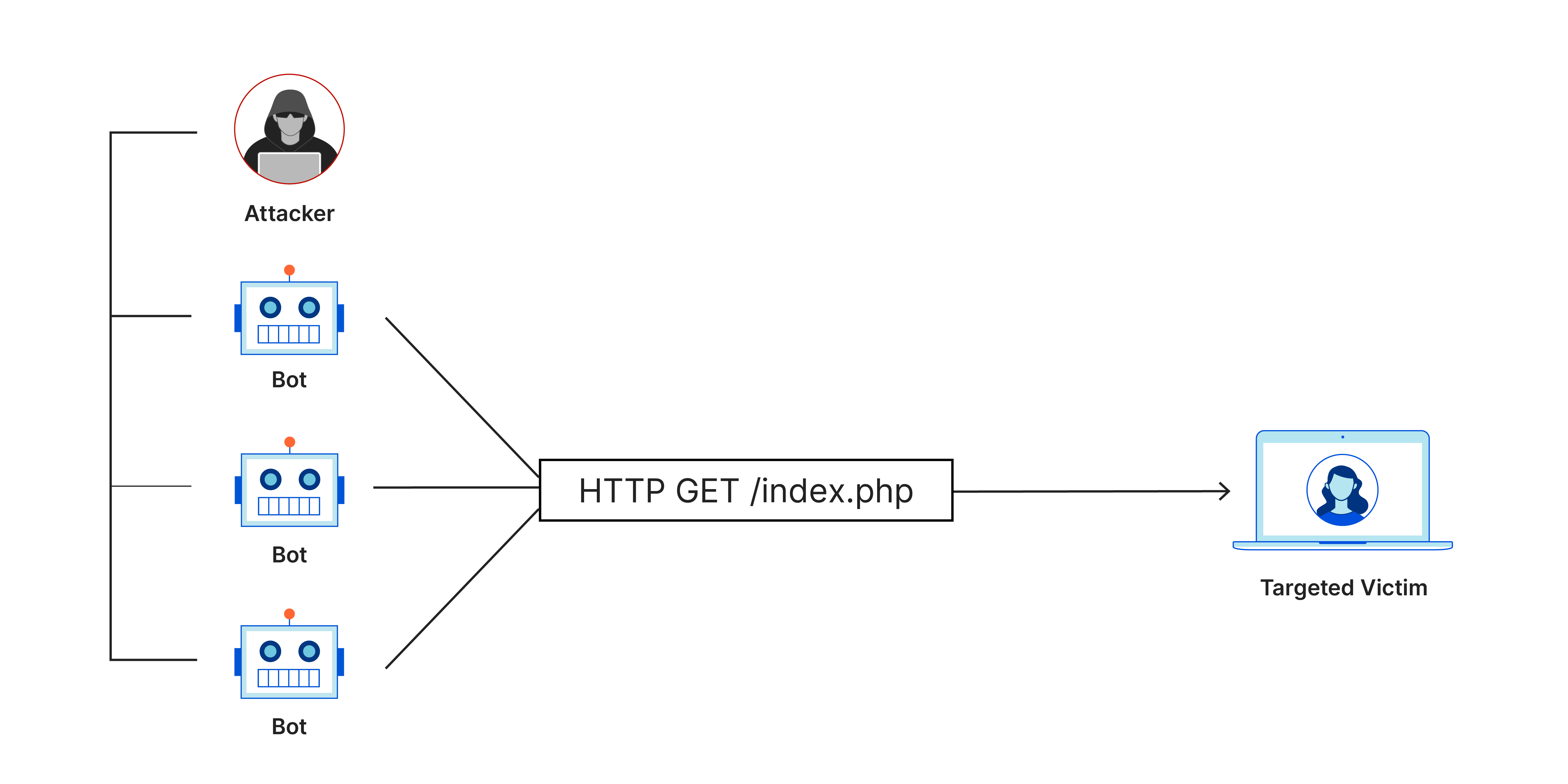
To address or prevent DDoS attacks, one has to filter traffic, limit the rate, and/or spread out the traffic load to be handled. Other types of DDoS attacks are well handled by cloud-based DDoS protection services as well.
Brute-Force Attacks
Brute force attacks are executed when the attacker uses programs to try to enter the username and password till he gets authorized access to an account. This method is very effective when the passwords used are very weak and, most importantly, passwords that are recurrent to other accounts. Moreover, Verizon also stated in their report that 81% of hacking-related data breaches were the result of theft of passwords or the use of weak passwords.
Encrypted passwords should be used, and passwords should be changed from time to time to ensure that someone searching for an easy way to crack a password does not easily find one, as recommended by Kankipat et al. Also, the account lockout that is done each time the user tries to log in with the wrong password for a given number of attempts will disable the use of brute force attacks.
Software Misconfigurations
It is estimated that the majority of web applications are vulnerable to software misconfigures. These can, for example, be having default passwords as they are, having services not applicable to the system, or not installing the most recent security updates. Most of the misconfigurations occur because of human intervention, and therefore the security scan and audit are important to eliminate the problem.
Configuration errors also apply to cloud services; wrong storage settings make data leave them open to the public domain. Since the increase in cloud solutions is constant, proper configuration should be adopted to increase the security of cloud web applications.
Methods of Protection
Input validation has to do with the to process data and the results of tests that have to do with the authenticity of the data before they are accepted.
Among the basic but efficient methods of threat protection are input validation and sanitization. Input validation means that user inputs are validated before the system accepts them as part of the processing so that bad data are not executed. Using input validation makes it possible to protect the application against many dynamic attacks, such as SQL injections and cross-site scripting.
For businesses seeking comprehensive security solutions, overcode provides expert services that integrate security at every stage of development, ensuring web applications are built with the highest level of protection.
Privacy of Electronic Commerce and Internet Transactions
Multi-factor authentication (MFA) that provides robust and more rigorous measures for fortification of the user’s accounts from brute-force attacks must be implemented. Developers should also check that user roles and permissions are set in such way that users can access only these resources for which they have rights to.
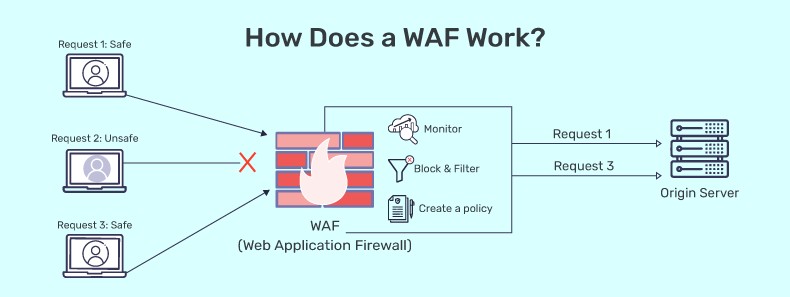
Web Application Firewall (WAF)
A web application firewall (WAF) therefore can be defined as an apparatus that analyzes and moderates traffic between a web application and the global web. WAFs will effectively filter out many attack types, such as SQL injection, XSS and Ddos attacks. A WAF would help developers ensure that there is an additional security measure governing the Web applications.
Encryption
If data is intercepted or has been stolen, it cannot be read by those who are not supposed to see it; this is the essence of data encryption, both transmitted and stored. Communications established with the user should be encrypted by using HTTPS and sensitive data stored in a database should also be encrypted.
Every six months, there should be a Security Audit and Penetration Testing
Security is a continuous process, and to make sure that the holes are known and patched before they can be exploited, then security audit needs to be done periodically. The method usually involves a simulated act of actual attacks with a view of evaluating the strength of security frameworks. Furthermore, through routine provision of these tests, the developers are in a position to confront new threats.
OWASP as a Security Standard
OWASP, the Open Web Application Security Project, is an organization that is focused on the issue of security in software products. One of OWASP’s significant contributions to web application security is its Application Security Verification Standard (ASVS), which specify for developers what must be done to be deemed secure.
Another should be read by developers: the list of OWASP Top 10 Security Risks. A list of these most important web application threats includes injection, inauthentication, security misconfiguration, etc. In this way, following the recommendations of the OWASP, developers are able to create web applications that will be resistant to the most frequent types of attacks.
For more information on OWASP’s security guidelines, you can visit their official website at OWASP ASVS.
Final Words
Security is one of the core aspects of web development and can hardly be overestimated at the moment. Since threats are continuously existing in cyberspace, developers have to become familiar with current security threats and how to avoid them.
However, implementation of the relative security standard, such as OWASP, would offer a good starting point of creating secure web applications. Again, safety entails constant measures rather than one or two activities of chasing away hoodlums during resulting celebrations.

