How to develop and secure Cloud apps?
How can businesses build cloud applications that are both reliable and secure? Organizations face a dual challenge: they must develop scalable solutions and protect sensitive data. As more businesses migrate to cloud-based infrastructures, they must adopt strong cloud solutions development and security practices. These steps help them maintain operations and preserve customer trust. In this article, we guide you through proven strategies and best practices. We show how you select the right architecture and implement advanced security measures. This guide helps you as you create cloud solutions that achieve high performance and withstand emerging threats.
Key advantages of cloud solutions for businesses
When businesses adopt cloud solutions, they revolutionize their operations and unlock benefits that were previously unattainable.The global adoption rate of cloud services continues to rise, with studies showing that 94% of enterprises already use cloud technologies in some form. To ensure your app adheres to mobile app security standards, developing cloud applications is now a key focus for organizations that aim to stay competitive.
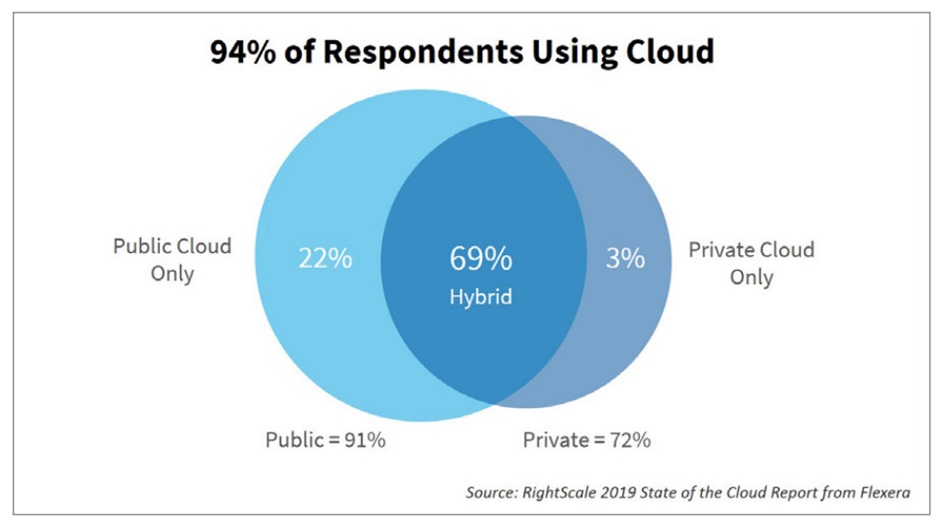
Source: Right Scale’s annual State of the Cloud Report
Here are the reasons why businesses increasingly embrace cloud solutions:
- Cloud solutions reduce the need for upfront investments in physical hardware and IT infrastructure. Businesses move to a pay-as-you-go or subscription-based model. This shift reduces capital expenses and allows them to direct resources toward growth. This choice proves particularly beneficial for startups and small companies, as they avoid the financial burden that arises when they purchase and maintain expensive servers. If you know how much does it typically cost to create a mobile app it can further guide budget planning in cloud solutions development.
- Cloud platforms let businesses scale resources dynamically based on demand, and they support periods of growth or temporary spikes in usage. Whether companies scale up during peak seasons or scale down during quieter periods, they gain the flexibility to match resources with their needs.
- Cloud-based tools make collaboration seamless, and teams now work together in real-time, regardless of location. Features that allow document sharing, integrated version control, and instant communication boost productivity and improve how teams function, especially when they operate remotely or in distributed settings.
- Cloud solutions grant unparalleled access to data and applications, and employees now operate from any location that has an internet connection. This flexibility supports arrangements in which employees work remotely and keeps business operations running without interruption, even during emergencies or travel.
- Leading cloud service providers invest heavily in advanced security protocols. These protocols cover data encryption, multi-factor authentication, and frequent backups. Such measures protect sensitive information and also allow rapid recovery when hardware failures, cyberattacks, or natural disasters occur.
- Cloud platforms streamline the quick adoption of new technologies like artificial intelligence, machine learning, and IoT. Businesses experiment with and deploy innovative solutions faster. This approach helps them remain ahead in competitive markets.
Cloud solutions are no longer a luxury but a necessity for businesses aiming to thrive in a rapidly evolving environment. They reduce costs, foster innovation, and serve as indispensable tools for growth and sustainability.
How to develop a cloud application
The process of developing cloud applications requires careful planning and execution that address scalability, security, and adaptability. Whether you aim to improve collaboration, automate workflows, or centralize data, the effort must align with both business goals and user needs. For those looking to streamline cloud app development, the following step-by-step guide describes the key stages that produce reliable cloud applications, with each phase designed for long-term success.
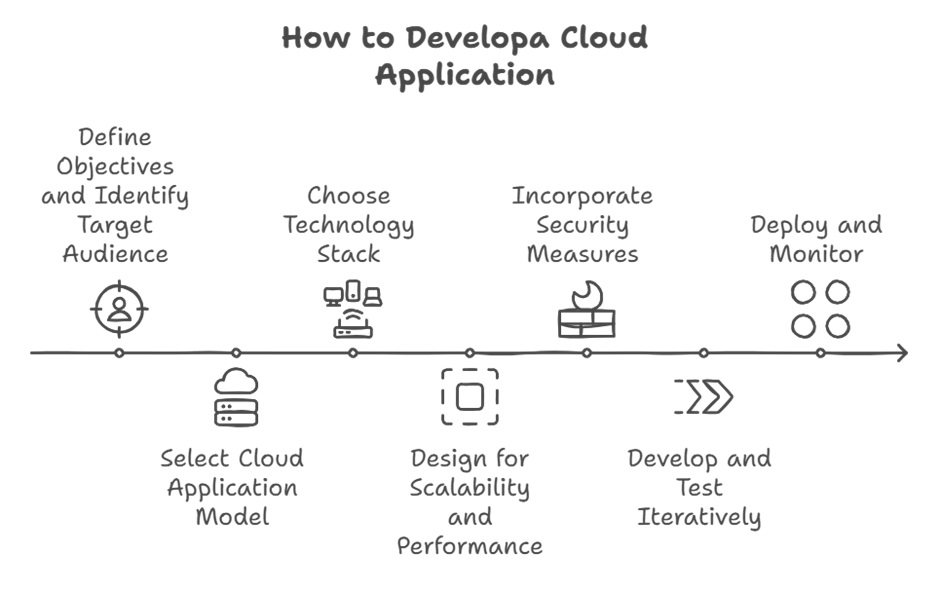
Created using napkin.ai
Step 1. Define objectives and identify the target audience
The foundation of a successful cloud application lies in a clear view of its purpose and audience. This process begins when you identify the core business goals the application aims to achieve. You should determine whether it solves a specific problem, improves workflows, centralizes data storage, or boosts collaboration across teams. Focus on the target audience’s preferences, technical expertise, and challenges, and then shape the app’s functionality accordingly. Establish priorities early on. Assess the importance of time-to-market, and use these insights to guide the development process.
Step 2. Select the right cloud application model
The choice of architecture forms the foundation of the application. For small-scale projects, a monolithic architecture might be suitable, though it may limit scalability. Applications requiring modularity and flexibility benefit from microservices architecture, where independent services handle specific functions. Event-driven apps with fluctuating demands perform well with serverless architecture, eliminating the need for server management. Hybrid cloud architecture, which combines on-premises and cloud resources, provides high flexibility, making it ideal for specific operational needs.
Step 3. Choose the technology stack
The technology stack has a big impact on performance, scalability, and maintainability. Common options include languages like Java, Python, or Node.js; databases such as MongoDB or MySQL; and frameworks like Django or React. It is important to evaluate the stack based on the development team's expertise and the complexity of the application. Consideration should also be given to tools like Kubernetes for container orchestration to streamline deployments and scaling.
Step 4. Design for scalability and performance
Scalability and performance should be integral to your application’s design. Distributed architectures allow workloads to be handled by multiple servers, reducing the risk of bottlenecks. Similarly, caching mechanisms improve response times by storing frequently accessed data. Stateless design, which eliminates the need for session data storage on servers, simplifies scaling and maintenance. The application should be capable of handling increasing user demands without any impact on performance for a smooth functionality during peak loads.
Step 5. Incorporate security measures from the outset
Security stands as a priority at every stage of development. First, set up authentication and authorization mechanisms that restrict unauthorized access. Also, use advanced encryption protocols, and encrypt data both in transit and at rest. Write secure code that avoids vulnerabilities. Perform regular security audits that identify and address potential risks. If you incorporate these measures early in the development process, you reduce the likelihood of breaches and build user trust in your application.
Step 6. Develop and Test Iteratively
Adopt an Agile or DevOps approach to streamline development. Agile focuses on iterative improvements through short development cycles, while DevOps integrates continuous deployment and testing for efficient workflows. Rigorous testing, including performance, usability, and security assessments, helps identify vulnerabilities early and avoids costly fixes later in the development lifecycle.
Step 7. Deploy and Monitor
Deployment occurs when the team launches the application into the chosen cloud environment, and this process allows a seamless transition. Tools that monitor resource utilization, system health, and user activity operate in real-time. Mechanisms that record logs serve an important role since they help the team identify anomalies and improve performance. These practices help to achieve reliable cloud solutions development and keep the application responsive under varying workloads.
Remember, cloud applications require continuous maintenance so that they remain relevant and secure. Periodic updates address vulnerabilities and improve functionality. Regularly, you can monitor performance, and this process helps identify potential bottlenecks or inefficiencies in resource allocation. When teams optimize the application, it remains stable even as user demands grow. Remain informed about advancements in cloud technologies and industry trends, to find opportunities for new features or the improvement of the existing capabilities.
5 Best practices to make cloud applications secure
According to the report, the global cloud market will likely reach $1.24 trillion by 2027, and this growth increases the importance of securing cloud applications. As businesses rely more on cloud platforms and handle sensitive data and workflows, cyberattacks occur with greater frequency and sophistication. Studies show that 60% of small businesses that experience a data breach close within six months. This fact underlines the need for strong security measures.
This section outlines practical practices to protect cloud applications against threats, address regulatory compliance, and maintain operational resilience. From timely updates to disaster recovery planning, these strategies tackle the challenges of modern cloud environments.
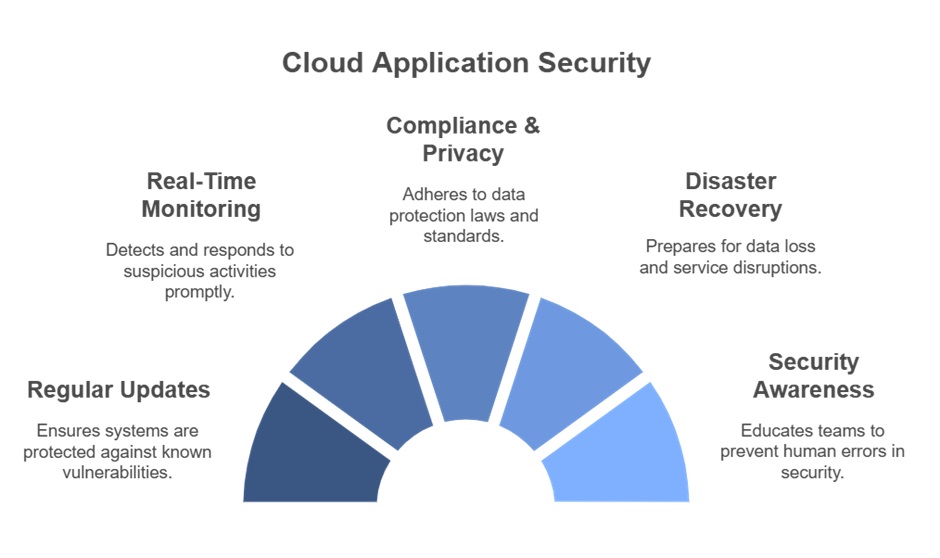
Created using napkin.ai
Regularly update and patch systems
Outdated software is a common entry point for cyber threats. Maintain an up-to-date system by applying vendor-released security patches and updates promptly. This practice addresses vulnerabilities that attackers may exploit. Periodic reviews of system configurations help eliminate outdated settings that could compromise application security.
Integrate real-time monitoring and intrusion detection
Monitoring systems, coupled with intrusion detection tools, help identify suspicious activities in real-time. Use logging mechanisms to record user activities and system events, providing insights into unusual patterns or anomalies. Automated alerts enable swift responses to potential threats, reducing the likelihood of data breaches.
Address compliance and privacy requirements
Cloud applications often operate in regulated industries, making compliance with data protection laws like GDPR, HIPAA, or PCI DSS very important. Adopt measures such as data anonymization, encryption, and clear access controls to align with regulatory standards. Frequent audits and documentation of security practices further demonstrate adherence to compliance requirements.
Plan for disaster recovery and business continuity
Regular backups are absolutely nessesary in case of data loss caused by breaches, hardware failures, or accidental deletions.These backups should be stored in secure, isolated environments, such as encrypted cloud storage or offline repositories, to protect them from unauthorized access or corruption. A disaster recovery plan is equally important, detailing the steps to restore services and minimize operational disruption. This plan should include clear roles and responsibilities, predefined timelines, and tested procedures to streamline recovery efforts.
Educate teams on security awareness
Human error remains one of the most common causes of security breaches. The organization should create a culture of security awareness among development teams and employees, as this approach reduces risks. Developers learn secure code practices and avoid vulnerabilities related to injection attacks, insecure dependencies, and improper input validation. Hold regular workshops or seminars that address emerging threats and offer strategies that counter them. All employees receive should know how to detect phishing attempts, how to protect login credentials and manage sensitive data responsibly.
Conclusion
The process of cloud solutions development has become indispensable for modern businesses. Whether you want to create cloud applications for collaboration, automate workflows, or centralize data management, you can achieve success only when it combines strategic plans with advanced security practices. By following the strategies discussed in this guide, businesses can develop cloud-based applications that meet their goals and are capable of withstanding modern challenges.
FAQ
How does application development on cloud platforms differ from traditional methods?
Application development on cloud platforms offers flexibility and scalability compared to traditional methods. Cloud platforms allow dynamic resource allocation, which enables businesses to adapt to changing demands without the need for additional hardware. This model also supports collaboration and remote accessibility, which are often limited in traditional setups.
What are the most common security challenges in cloud applications?
Key challenges exist in the form of data breaches, insider threats, and insecure APIs, and these incidents expose sensitive data and disrupt operations. You can addresses these threats with strong encryption, real-time oversight, intrusion detection, and updates that remove vulnerabilities. When you adopt a Zero Trust security model, it further reduces risks, because it verifies access at every step and restricts permissions to only what each user or process requires. This layered approach protects against both external and internal threats, and it keeps the application secure.
What are the initial steps to develop cloud-based applications?
The first steps are to define clear objectives, identify the target audience, and select a suitable architecture. Determine the application’s purpose—is it meant to streamline workflows, improve collaboration, or centralize data? Decide between a monolithic, microservices, or serverless architecture so that the application aligns with both technical and business goals.

