Simplify Network Management with a Single Source of Truth
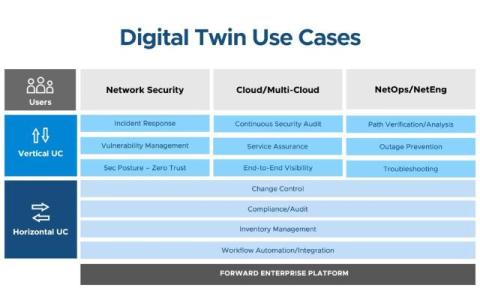
Managing complex networks can feel like an endless challenge, especially when critical data is scattered across multiple tools and systems. Conflicting sources of truth (SOTs) introduce risks, leaving IT teams uncertain about which data to trust. Without an accurate view of your network, tasks like CVE management, troubleshooting, and compliance become overwhelming—and potentially introduce risk into the network.