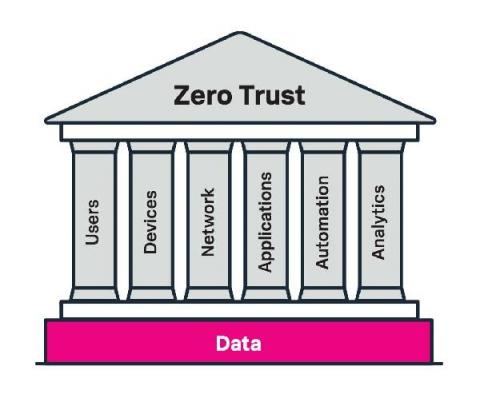
"Zero Trust" is an Adjective in Search of a Noun
People love to talk about zero trust right now, for a number of reasons. It has the word “zero” in there, which has some history in the information security world (e.g., zero-day vulnerabilities). It’s also a simple and eye-catching phrase, so it fits well into product marketing exercises.