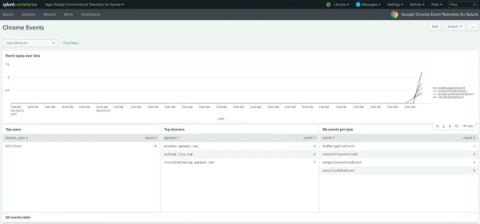
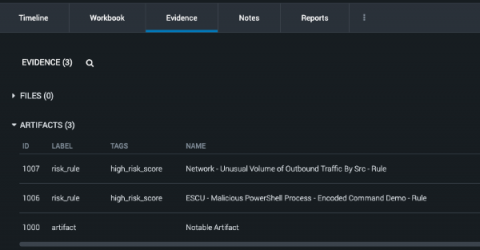
RCE à La Follina (CVE-2022-30190)
If you want just to see how to find detections for the Follina MS Office RCE, skip down to the “detections” sections. Otherwise, read on for a quick breakdown of what happened, how to detect it, and MITRE ATT&CK mappings.