Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
December 2021
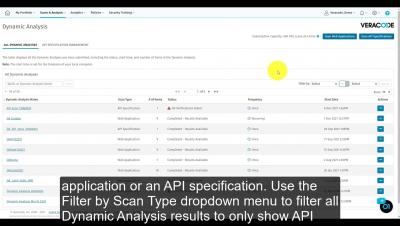
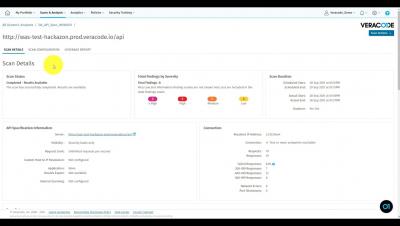
Review API Scanning Results
A Review of Log4Shell Detection Methods
Ever since the public exploit of the Log4Shell remote code execution (RCE) vulnerability became known on December 10, 2021, security teams have been scrambling to understand the risk to their environments. Part of that scramble has been to ascertain which tools are best positioned to help detect the vulnerability. Which approaches are most effective and where do they fall short?
Looking ahead to 2022
Part 4: Using Veracode From the Command Line in Cloud9 IDE
It’s Clint Pollock, principal solutions architect, here for the final lesson in the four-part series on how to use Veracode from the command line in the Cloud9 IDE to submit a software composition analysis (SCA) scan and a dynamic scan. To start, if you’re looking to leverage the Veracode API signing docker image with the Veracode rest APIs, go to the Help Center, go to the Rest API section, and take a look at the available options.
The Good, the Bad, and The Ugly: Understanding the API Security Top 10 List
The Open Web Application Security Project (OWASP) is a nonprofit organization with the purpose to help secure software. They provide data that can give engineering and security teams a better idea of where the most common risks may lie. The 2021 OWASP Top 10, released in November 2021, lists the most critical web application security risks. But OWASP also maintains the API Security Top 10 project which was last updated in 2019. Each category is ranked based on the frequency and severity of the defect.
58% of Orgs Are Using a Vulnerable Version of Log4j
On December 9, 2021, a zero-day vulnerability in Log4j 2.x was discovered. This vulnerability is of great concern because if it’s successfully exploited, attackers are able to perform a RCE (Remote Code Execution) attack and compromise the affected server. Since we are a cloud-based Software Composition Analysis (SCA) provider, we have useful customer data that gives insight into the scope of the Log4j vulnerability.
Security Update: Log4j.2.x Vulnerability
SECURITY NOTICE: Log4j.2.x NEWS
URGENT: Analysis and Remediation Guidance to the Log4j Zero-Day RCE (CVE-2021-44228) Vulnerability
A previously unknown zero-day vulnerability in Log4j 2.x has been reported on December 9, 2021. If your organization deploys or uses Java applications or hardware running Log4j 2.x your organization is likely affected.
Part 3: Using Veracode From the Command Line in Cloud9 IDE
In part three of a four-part series, Clint Pollock, principal solutions architect at Veracode, details how to use Veracode from the command line in the Cloud9 IDE to submit a software composition analysis (SCA) scan. Check out the video and step-by-step instructions below. It’s Clint Pollock, principal solutions architect, back again for part three of our four-part series on using Veracode from the command line in Cloud9 IDE.