The Path of an Outlaw, a Shellbot Campaign
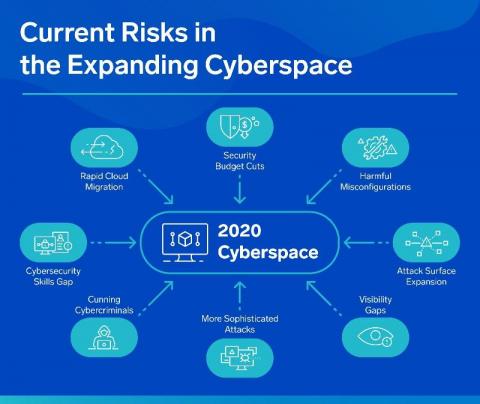
The ability of an actor to remain undiscovered or obfuscating its doings when driving a malicious campaign usually affects the gains of such campaigns. These gains can be measured in different items such as time to allow completion of operations (exfiltration, movement of compromised data), ability to remain operative before take down notices are issued, or ability to obtain gains based on for-profit driven crimeware (DDoS for hire, Crypto mining).