Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
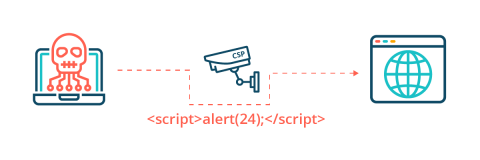
A Pen Tester's Guide to Content Security Policy
In this article, we’ll look at Content Security Policy through the eyes of a penetration tester. We will outline the advantages of CSP, explain why you should have it on your site, and share some common misconfigurations that can be exploited, along with the relevant bypass scenarios. What is Content Security Policy?
How Code Coverage Helped Me Find 3 SQL Injections
Snyk's AppSec journey in 2022
Coming off a rough and wild end to 2021 with Log4Shell in all our minds, Snyk jumped out of the gates quickly and began providing the AppSec world with new capabilities that did not disappoint. In this blog, you can review most of the key investments we made in 2022 to improve performance, add new ecosystems, and support the enterprise.
Bolstering Snyk's developer security platform in 2022
2022 was another record-breaking year for the Snyk platform. Helping an ever-growing number of customers find and fix issues across all the components making up their applications, the Snyk platform enabled over 2,500 customers during 2022 to import over 6.7 million projects, execute over 3 billion tests, and fix over 5 million issues!
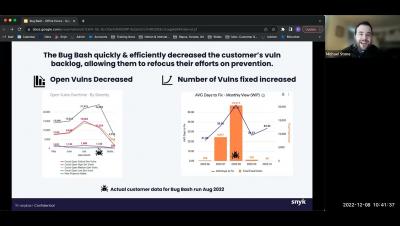
Bug Bash - How To & Best Practices - Snyk Customer Office Hours
CVE-2022-47523 - High Severity Vulnerability in ManageEngine Credential Management Products
Pen Test vs Vuln Scans - What's the difference? Cybersecurity 101
Supply chain security incident at CircleCI: Rotate your secrets
On January 4, CircleCI, an automated CI/CD pipeline setup tool, reported a security incident in their product by sharing an advisory.
Watch out for DoS when using Rust's popular Hyper package
The JFrog Security Research team is constantly looking for new and previously unknown vulnerabilities and security issues in popular open-source projects to help improve their security posture and defend the wider software supply chain.