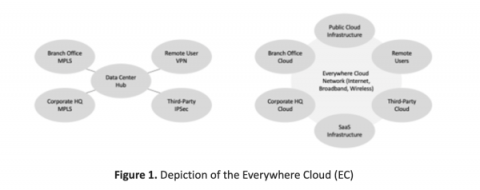
Nightfall Enables Advanced Secret Detection with Enhanced Machine Learning API Key Detector
Compromised secrets and credentials are the most common cause of data breaches and are often left unmanaged. In the past year alone, we’ve seen sustained growth in supply chain attacks and security incidents impacting the security of secrets stored in code repos or unknowingly shared within SaaS applications. Because of this, there is a compelling need for reliable, accurate, and actionable secrets detection for modern organizations.