Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
What's new in UpGuard | May 2021 | Cyber Security Product Releases
Synopsys
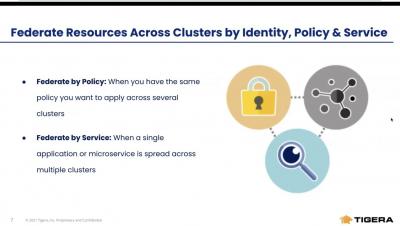
Unified Controls | Tigera
AppSec Decoded: Smarter DevSecOps with Intelligent Orchestration | Synopsys
The Rise of the PS5 Scalper Bots: An Analysis
Table of Contents In a webinar last December, Netacea’s Head of Threat Research, Matthew Gracey-McMinn, and Head of eCommerce, Tom Platt, joined forces to deep dive into the scale of the scalper bot problem, and the impact on the 2020 PS5 launch. If you missed the webinar, we’ve summarized the top takeaways for you here.
EPHEMERAL LOCKPICKER: Malware Leveraged for Novel Intrusion Lifecycle and LuckyDay Ransomware Delivery
In 2021, Kroll investigators have had multiple opportunities to respond to a series of interconnected network intrusions, ransomware events and cyber incidents which, upon investigation and review, possessed overlapping tactics, techniques and procedures (TTPs) and similar indicators of compromise (IOC) among them. The incidents affected organizations of various sizes across diverse industry sectors through what Kroll’s investigations confirmed was a range of separate intrusion vectors.
Creating An Audit Program In Today's Digital Landscape To Promote Compliance
In todays political landscape a more aggressive enforcement approach from health and safety regulators is fast approaching. For employers looking to reduce their business risk, achieving regulatory compliance starts with creating an audit program that is both strong and sustainable. However, with COVID-19 restrictions still in place, many organizations are facing new barriers that may impede how they assess compliance and limit their potential exposure.
What is the Coralogix Security Traffic Analyzer (STA), and Why Do I Need It?
The wide-spread adoption of cloud infrastructure has proven to be highly beneficial, but has also introduced new challenges and added costs – especially when it comes to security. As organizations migrate to the cloud, they relinquish access to their servers and all information that flows between them and the outside world. This data is fundamental to both security and observability.