Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Kondukto
A Look into Modern Security Orchestration
AppSec Talks - Episode 1 with Rami McCarthy - Figma
Create SBOM on Gradle with the CycloneDX Plugin
Enhancing Security with eBPF: Use Cases Explored
How Malicious Code Enters Applications
As the backbone of modern business operations, applications are frequently targeted by sophisticated malicious threats. In this blog post, we provide a high-level overview of how malicious code can enter your software applications. We look at different forms of malicious code, their entry points, practical tools and strategies for detection & prevention, focusing on innovative solutions.
ASPM and Security Testing Orchestration
Considering the complexity of the modern application stack and developer tooling, ensuring the security of your application throughout its lifecycle can quickly become a daunting task.
Container Security: A Quick Overview
Container security is an increasingly vital aspect of modern software development and deployment. Understanding and implementing effective security measures becomes essential as organizations shift towards containerizing their applications. This article will explore practical insights and strategies for ensuring robust container security. We will delve into some best practices and tools to secure container environments, focusing on securing images and registries, container deployment, runtime security, and more.
Unveiling Java Library Vulnerabilities
During a recent customer engagement, we encountered an interesting situation. The customer had raised concerns about a Java XXE (XML External Entity) vulnerability that had left their developers puzzled. Notably, their Static Application Security Testing (SAST) scans consistently identified this as a potential vulnerability.
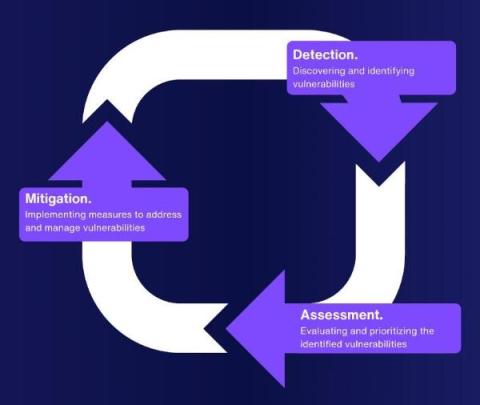
How to Streamline Vulnerability Management
The current cyber world is a veritable minefield, with problems and dangers evolving at a rate that far outstrips the ability of most organizations to respond. More than merely a technical issue, an organization's security posture is determined by the quality of its vulnerability management.