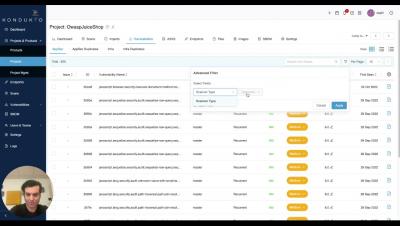
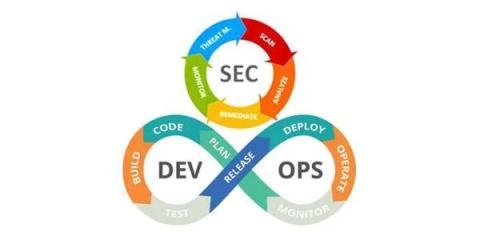
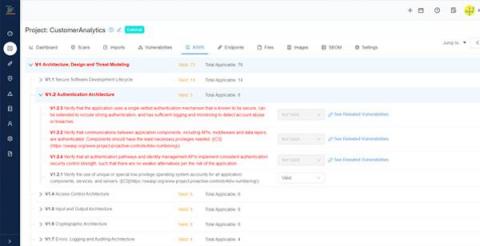
How to integrate continuous API fuzzing into the CI/CD?
API security is a growing concern for businesses that offer or consume APIs. APIs, or application programming interfaces, allow different software systems to communicate and exchange data. They allow businesses to build integrations and connect with partners, customers, and other stakeholders. However, as more sensitive data is being shared through APIs, it is essential to ensure that these interfaces are secure and protected from unauthorized access or manipulation. In this blog post, we'll discuss how continuous fuzzing can be a powerful tool to secure APIs and how developers can adopt a "secure by default" approach by integrating continuous fuzzing into SDLC processes.