Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SBOM
In the age of AI, how do you know what data to trust?
Last week, the godfather of AI, Geoffrey Hinton smashed the glass and activated the big red AI alarm button warning all of us about creating a world where we won’t “be able to know what is true anymore”. What’s happening now with everything AI makes all the other tech revolutions of the past 40 plus years seem almost trivial.
Instaproof in action! Drag. Drop. Verify!
Instaproof in action! Drag. Drop. Create!
RKVST Instaproof - instant data provenance
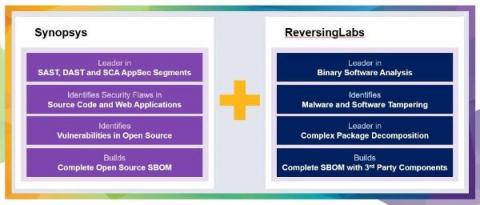
Synopsys and ReversingLabs sign agreement to enhance software supply chain risk management
A Guide to Standard SBOM Formats
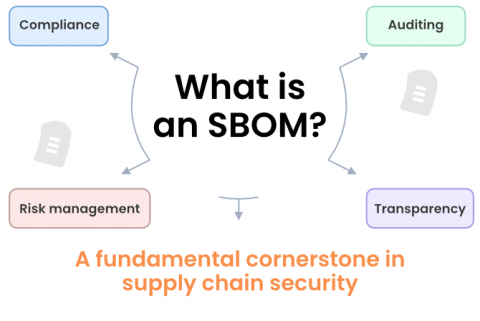
The software bill of materials (SBOM) has become an increasingly important tool for providing much-needed clarity about the components that make up software — both for application security purposes and governmental compliance. Unlike manual spreadsheets, SBOMs standardize everything into a particular format to minimize inconsistencies. There are three primary SBOM formats currently available, which allow companies to easily generate, share, and consume SBOM data.
What is Software Bill of Materials (SBOM) & Why Is It So Important?
Computer software is a complicated construct composed of numerous diverse components. Open-source software is becoming ever more common as a building block in software. This phenomenon is accompanied by an increase in exploitable vulnerabilities, so being able to tell quickly what your software is composed of is becoming increasingly important - both in applications that you develop yourselves and the ones from suppliers and vendors.
Hands-on guide: How to scan and block container images to mitigate SBOM attacks
According to OpenLogic’s Open Source Adoption and Expansion in 2022 Report, the adoption of Open Source Software (OSS) across all sizes of organizations is rising with 40% of respondents stating an increase of OSS software over the previous year and 36% reporting a significant increase in OSS software usage. The increase in OSS adoption can be attributed to a number of factors including access to the latest innovations, reduction in costs and frequent product updates.