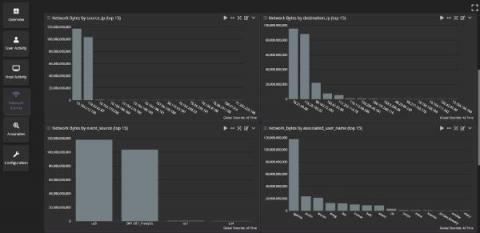
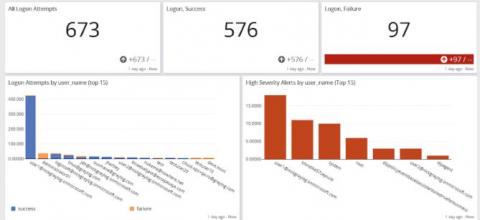
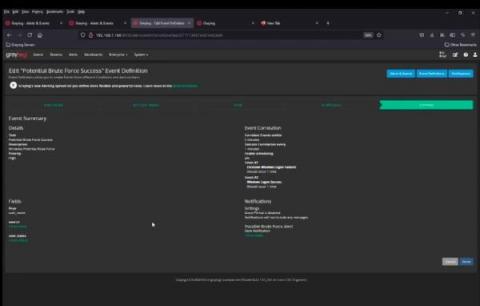
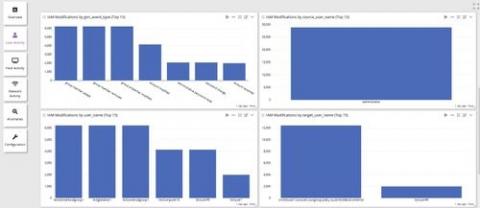
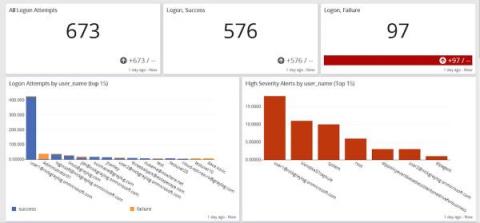
Centralized Log Management for Data Exfiltration
Remote workforce models don’t look like they’re going anywhere anytime soon. While your employees need to collaborate, you need to make sure that you mitigate data breach risks. You worked diligently over the last few years to put the right access controls in place. The problem? Data breaches aren’t always threat actors and are not always malicious.