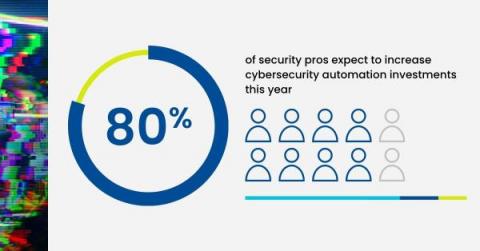
Why Security Leaders are Betting on Automation
Mass layoffs. Budget cuts. Funding shortages. Fears of recession. Headlines paint a bleak picture for organizations in 2023. To prepare for the turbulent year ahead, companies are scaling back their spending in droves. Yet, amid ruthless cost-cutting, many organizations are still prioritizing their investments in bulking up cybersecurity defenses. The question is, what are they spending these budgets on?