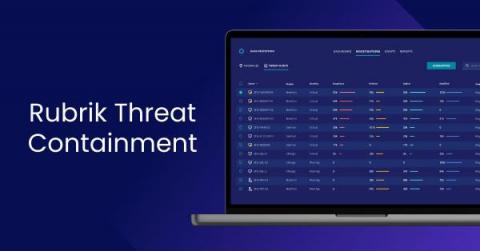
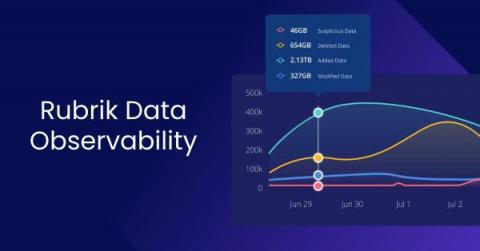
Become Unstoppable with the Rubrik Data Security Command Center
From technology to healthcare to governments, ransomware is disrupting business like never before. Security teams are reevaluating their overall security posture and taking additional measures to secure their data. During this process, they are discovering that they don’t know if their organization’s data is fully secure and whether it will be available when they need it.