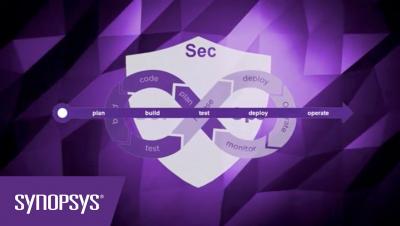
The BSIMM: Five key steps to a better software security initiative
If you care about software security—and you should, since to be in business today means that no matter what you do or produce, you’re also a software company—you should be interested in the Building Security In Maturity Model (BSIMM). It can serve as a roadmap to better security.