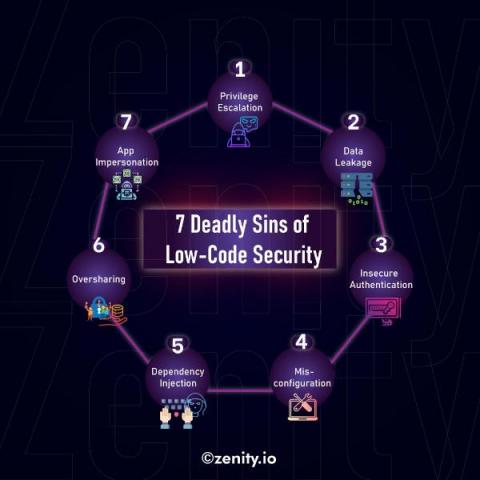
Is Credential Sharing the Weakest Link in Your Security Strategy?
You might think that the majority of cybersecurity breaches result from carefully planned and executed attacks. You may imagine hackers expertly crafting phishing emails to con employees into giving away access to critical systems, for example, or planting state-of-the-art malware on victims' servers. The reality – as Zenity co-founder and CTO Michael Bargury explains in his most recent Dark Reading column – is less interesting, and perhaps more worrying.