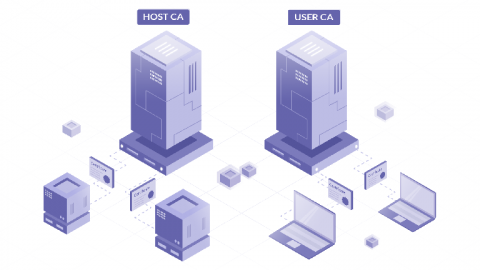
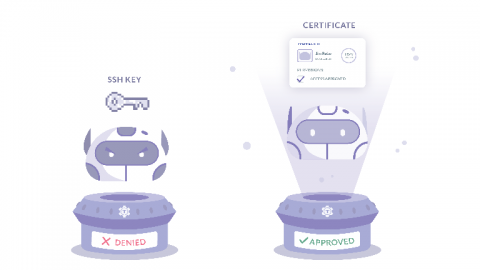
How to SSH Properly
There’s no denying that SSH is the de facto tool for *nix server administration. It’s far from perfect, but it was designed with security in mind and there’s been a huge amount of tooling written over the years to make it easier to use. In addition, many popular products and just about every server deployment system integrates with SSH somehow.