Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Teleport
Teleport 10
0:00 Introduction
0:15 Passwordless Access
0:48 Access Requests
1:35 Snowflake Access
2:23 Teleport Server Access
3:15 Learn more
Securing MySQL Databases with SSL/TLS.
Many databases were born over 25 years ago, back in the unadulterated times of LAN parties and IRC. SSL was just for banks and sending unencrypted database traffic accounts was just how you did things. When databases use unencrypted connections, it means someone with access to the network could watch all and inspect all database traffic.
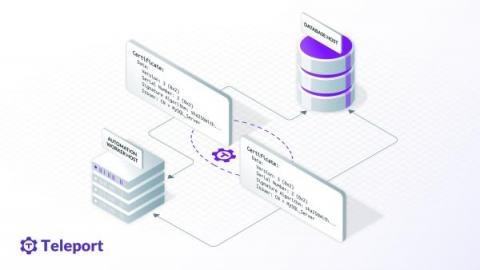
Production MySQL SSL with Teleport Machine ID
In the first part of this blog post, we setup SSL/TLS for a MySQL database, using the built in self-signed certificates. The main problem using out of the box self-signed certificates is that clients can't verify that they're talking to the right database host, and it's not possible to verify the certificate chain. In this post we'll cover upgrading the client connection to VERIFY_IDENTITY and how to use Machine ID to continuously renew certificates.
Securing Microsoft SQL Server
Microsoft SQL Server is a popular relational database management system created and maintained by Microsoft. It’s effective in numerous use cases: storage and retrieval of data as part of a DBMS, transaction processing and analytics applications. However, there are some essential measures you must take to protect your database from cybercriminals and security breaches, as the default security settings are relatively insufficient to keep your database safe.
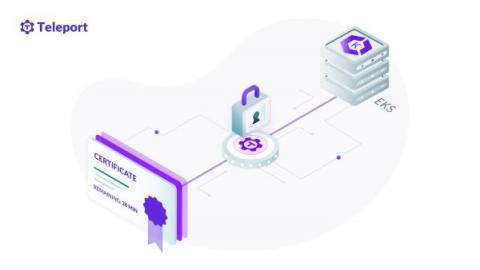
Secure Amazon EKS Access with Teleport
Enterprises are embracing the cloud native paradigm for agility, scalability, composability, and portability. Kubernetes, the open source container orchestration engine, is the foundation of modern, cloud native workloads. AWS customers can leverage managed Kubernetes available in the form of Amazon Elastic Kubernetes Service (EKS) or deploy a cluster based on upstream Kubernetes distribution running in a set of Amazon EC2 instances.
Trustless Infrastructure: Securing Critical Assets with Teleport
What You Need to Know About X11 Forwarding
X11 forwarding, ssh -X, is an SSH protocol that enables users to run graphical applications on a remote server and interact with them using their local display and I/O devices. It is commonly relied upon by developers for securely interacting with remote machines across wide and heterogeneous server fleets.
Teleport Demo - 30 Minute Overview
0:00 Intro
1:00 Architecture Overview
3:00 Single Sign On Integration
5:00 Teleport Server Access
7:00 tsh and session recordings
9:00 Teleport App Access
11:00 RBAC Mapping
12:05 Teleport K8s Access
15:00 Teleport DB Access
18:00 Teleport RDP Access
22:00 Access Requests
24:00 Teleport Slackbot
26:00 Active Session Joining
27:00: Trusted Clusters
28:00 Open Source vs Enterprise
WebAuthn Explained
The WebAuthentication API, or WebAuthn, facilitates secure authentication based on public-key credentials. The idea of passwordless and public-key authentication is not new, but the compatibility and interoperability of various elements in the authentication process were always weak. WebAuthn API aims to solve that problem by bringing the uniform authentication API into web browsers.