Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
The future job market for cybersecurity professionals
If you work in IT – and even if you don’t – you’re probably aware of the huge shortage of cybersecurity professionals. Most companies are desperate for analysts trained to protect their valuable data from theft. On the surface, then, the future of the job market for cybersecurity seems bright. Look a little deeper, though, and you’ll see that this headline hides a lot of complexity.
Sysdig Secure Overview
What is Data Security?
Data security is the process of protecting sensitive data from unauthorized access and corruption throughout its lifecycle. Data security employs a range of techniques and technologies including data encryption, tokenization, two-factor authentication, key management, access control, physical security, logical controls and organizational standards to limit unauthorized access and maintain data privacy.
Attackers Using PureLocker Ransomware to Target Enterprises' Servers
Researchers have detected a new ransomware family they’re calling “PureLocker” which attackers are using to target enterprises’ production servers. Intezer detected a sample of the ransomware masquerading as the Crypto++ C++ cryptography library. In their analysis of the sample, they noticed something unusual when they saw that alleged library contained functions related to music playback.
Mitigating Risk and High-Risk Vulnerabilities in Unsupported Operating Systems: BlueKeep Edition
How many times has a vendor released a critical cybersecurity patch for an operating system that is in “end of life” (EOL), or the lifecycle period where the vendor no longer issues patches for bug fixes, operational improvements and cybersecurity fixes free of charge? So if a vendor takes the time and resources to break this freeze and issue a patch for an EOL operating system like it did in response to BlueKeep, what does it tell you?
How to Achieve Proactive Threat Hunting
Threat hunting practices are gaining much more importance as hackers and cyber threats focus on improving their stealth. As a result, it is essential for organizations to take on a proactive stance on threat hunting. Continue reading to learn how you can manage that. What is threat hunting? Threat hunting is one of the fundamental cyber security practices. It aims to detect stealthy attacks and threats that go undetected by the traditional security measures.
Can Google now guess your password in under 4 minutes?
In a recent story that appeared on multiple news sites, as well as the Google AI Blog, it was announced that Google has achieved “Quantum Supremacy” with its 54-Qubit processor, named “Sycamore”. This is a monumental leap forward in computing capabilities. (Yes, I had to resist calling it a quantum leap forward, because that does not nearly sum up this accomplishment). This is huge! The question exactly is, how huge?
Series A Financing to Continue Styra's Vision
This week, I'm pleased to announce that we closed our $14M Series A financing round. We look forward to partnering with our new investor, Accel, who led the round alongside existing investors, Unusual Ventures and A.Capital. Accel's Eric Wolford will join our board, bringing a wealth of open source experience from Heptio, SysDig and Corelight.
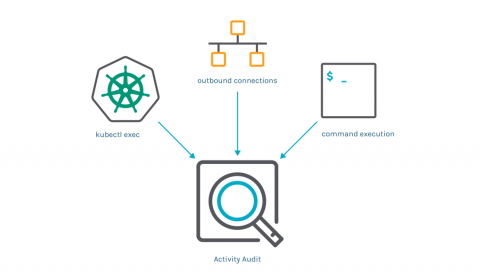
Incident response in Kubernetes with Sysdig's Activity Audit
Activity Audit is a new feature included in the Secure 3.0 release. This feature speeds incident response and enables audit by correlating container and Kubernetes activity.