CyberArk Endpoint Privilege Manager & ServiceNow Integration
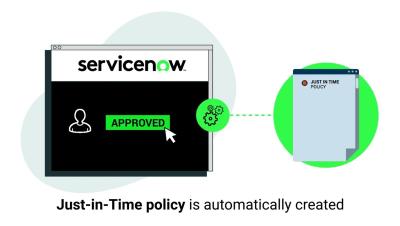
In this video, we delve into the seamless integration of CyberArk Endpoint Privilege Manager and ServiceNow IT Service Management. Discover how this integration streamlines and automates end user privilege elevation requests by leveraging existing ServiceNow workflows. By enhancing security measures and operational efficiency, this collaboration between CyberArk and ServiceNow marks a significant advancement in managing and securing privileged access. Watch now to learn more about this powerful integration.