Cyber Insurers Are Not Your Friend - Why a Warranty May Be a Better Option
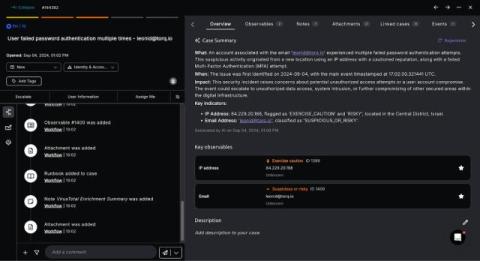
In this landscape, organizations need a multi-faceted approach that includes prevention, detection, and response capabilities. A warranty tied to a comprehensive security solution supports this approach, providing both technological protection and financial assurance.