Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
What Is Kubernetes Admission Control?
Kubernetes admission control is a mechanism that validates and modifies requests to the Kubernetes API server before they are processed. Admission control can enforce policies, security rules, resource limits, default values and other elements of the cluster’s use. This mechanism can also reject requests that violate certain rules or conditions.
Introducing Calico Runtime Threat Defense-The most extensive security coverage for containers and Kubernetes
Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
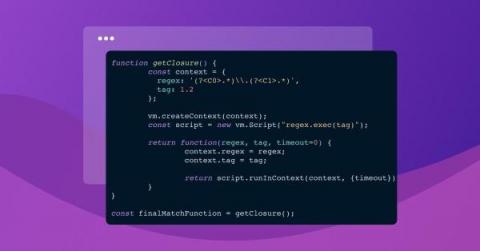
Timing out synchronous functions with regex
How hard can it be to support custom container image tags? Turns out… quite! I know this because my team has been busy at work on our new custom base image support for Snyk Container, andwe were tasked with the following problem: Given a tag, parse its parts to be able to compare it to other similar tags. It was a fun problem to solve, and we'd love to share how we got to our final solution!
GitOps with Styra DAS and OPA
The practice of infrastructure as code (IaC) has enabled platform teams to control infrastructure using code stored in Git. This enables teams to apply standard development practices like code review and testing to infrastructure management. The practice of GitOps takes this a step further by: Open Policy Agent (OPA), thanks to its Rego policy language, enables organizations to manage their authorization policies as code (PaC).
Proxyjacking has Entered the Chat
Did you know that you can effortlessly make a small passive income by simply letting an application run on your home computers and mobile phones? It lets others (who pay a fee to a proxy service provider) borrow your Internet Protocol (IP) address for things like watching a YouTube video that isn’t available in their region, conducting unrestricted web scraping and surfing, or browsing dubious websites without attributing the activity to their own IP.
OPA vs. Enterprise OPA: Why You Need Enterprise OPA
We recently released Enterprise OPA, the drop-in enterprise edition of Open Policy Agent (OPA). With Enterprise OPA, we aim to solve several challenges large organizations encounter when using OPA. These include performance and memory usage when using large datasets, keeping authorization data up to date and performing policy updates in a safe way.
4 ways to leverage existing kernel security features to set up process monitoring
The large attack surface of Kubernetes’ default pod provisioning is susceptible to critical security vulnerabilities, some of which include malicious exploits and container breakouts. I believe one of the most effective workload runtime security measures to prevent such exploits is layer-by-layer process monitoring within the container. It may sound like a daunting task that requires additional resources, but in reality, it is actually quite the opposite.
How to reduce your RPO and recover rapidly from failure on your K8s Cluster with Trilio and Mirantis
How to Detect SCARLETEEL with Sysdig Secure
The recent SCARLETEEL incident highlights the importance of detecting security threats early in the development cycle. With Terraform state files, attackers can easily access sensitive information and gain unauthorized access to your cloud infrastructure. In this case, the attackers exploited a containerized workload and used it to perform privilege escalation into an AWS account, stealing software and credentials.