Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SIEM
The latest News and Information on Security Incident and Event Management.
ManageEngine named a 2020 Gartner Peer Insights Customers' Choice for Security Information and Event Management!
We’re excited to announce that ManageEngine has been recognized as a Customers’ Choice in 2020 Gartner Peer Insights “Voice of the Customer’: Security Information and Event Management (SIEM) for the second time. This is in addition to our recognition in Gartner’s Magic Quadrant for Security Information and Event Management, 2020 for four consecutive times. We are thrilled to be named this recognition yet again. What better way to be recognized than by our customers?
What Data Types to Prioritize in Your SIEM
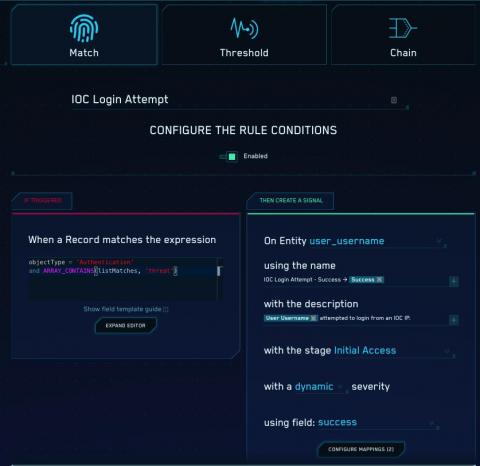
Cloud SIEM: Getting More Out of Your Threat Intelligence - 3 Use Cases for IOCs
Building a Security Practice Powered by Cloud SIEM
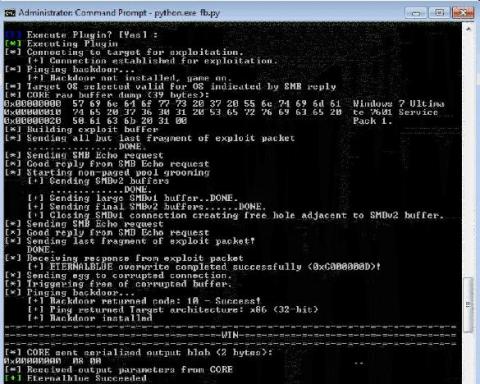
Defense in depth: DoublePulsar
Integrating Attack Behavior Intelligence into Logstash Plugins
Preventing "copy-paste compromises" (ACSC 2020-008) with Elastic Security
The Australian Cyber Security Centre (ACSC) recently published an advisory outlining tactics, techniques and procedures (TTPs) used against multiple Australian businesses in a recent campaign by a state-based actor. The campaign — dubbed ‘copy-paste compromises’ because of its heavy use of open source proof of concept exploits — was first reported on the 18th of June 2020, receiving national attention in Australia.