Analyzing EKS cluster data with Calico and SIEM to detect threats and improve security
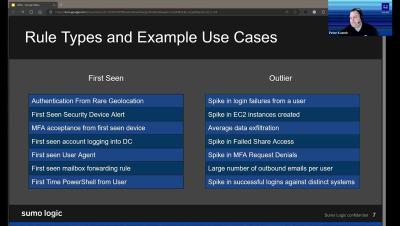
Security Information and Event Management (SIEM) is essential for enterprise organizations because it provides the tools and capabilities needed to effectively monitor, detect, respond to, and mitigate cybersecurity threats, while also supporting compliance and overall security strategy enhancement.