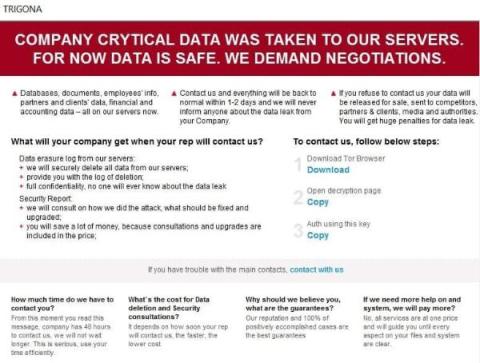
Anand's insight on Ransomware Threats
Listen to Anand Prahlad, CEO, Parablu Inc., share crucial insights into ransomware threats and how they impact SaaS companies of all sizes. Anand explains the reasons behind the increasing cybersecurity problem, focusing on industries frequently targeted. Anand also sheds light on: Watch this video to learn how to protect your business data against potential threats. Tune in now!