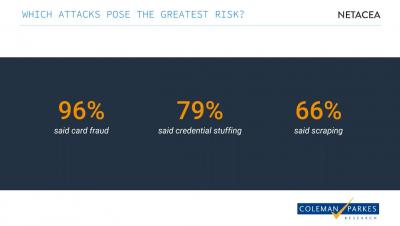
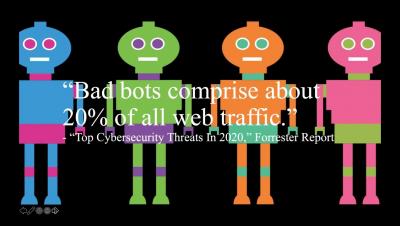
The Future of Cyber Security Manchester: What Are Bot Attacks?
Netacea's General Manager, Nick Baglin, talking about a new approach to bots and account takeover at The Future of Cyber Security Manchester 2019. This presentation will reveal the true extent of the bot problem and what you can do to solve it using behavioural machine learning that identifies even the most sophisticated bots.