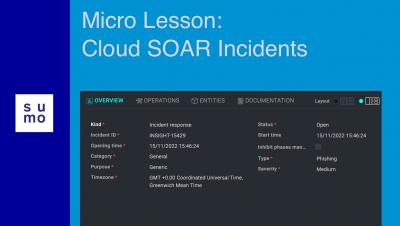
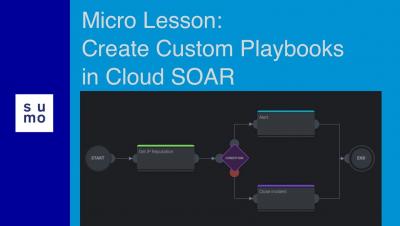
Micro Lesson: Sumo Logic Security Solutions
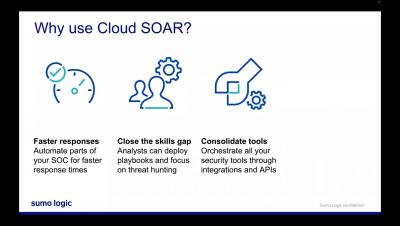
Learn about Sumo Logic's various security solutions: Cloud Security Monitoring & Analytics, Cloud SIEM, and Cloud SOAR. Each solution can help monitor, investigate, and respond to security incidents, but each also specializes in one of these areas.