Protect Users From Phishing and Malicious Content with Lookout
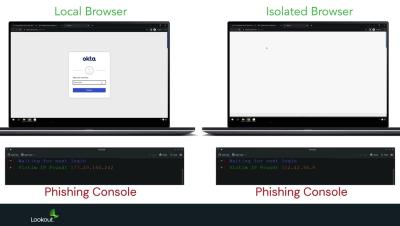
See how Lookout's phishing and content protection engine enhances security by blocking access to suspicious sites. Discover how remote browser isolation technology safeguards against zero-day phishing sites, preventing credential theft and malicious code execution on endpoint devices.