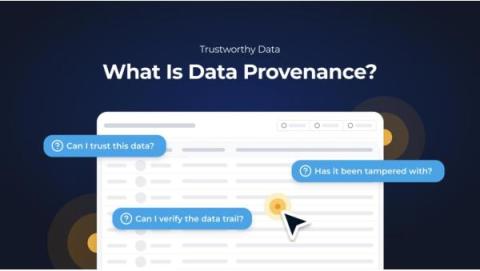
Three Easy Ways to Maintain Data Security and Compliance in NetSuite
Information is an organization’s most valuable asset — and with over 94% of US-based organizations using cloud-based systems, one data breach can have serious consequences for a growing business. Maintaining the integrity and security of your data should be high on your priority list — and luckily, with the right applications, getting there can be simple. NetSuite is a fantastic system for data security and compliance.