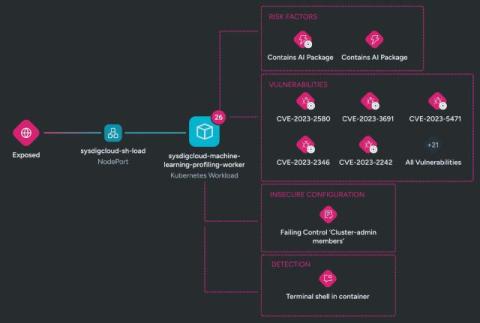
The key challenges of intrusion detection and how to overcome them
However, to achieve the full potential of this approach, they must first overcome a variety of challenges. Read on to discover what intrusion detection is and how it has evolved, plus the four key challenges associated with it and how to address them.