Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
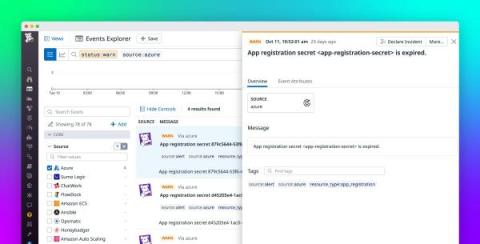
Monitor expiration events from Azure Key Vault
For customers using Azure Key Vault—which helps them safeguard sensitive keys and secrets used by applications and services hosted on Azure—it can be challenging to determine when the resources in their Key Vault(s) are about to expire. Invalid keys and secrets can disrupt your day-to-day workflows by causing application downtime, holding up incident investigations, invalidating compliance, slowing down the development of new features, and more.
Collect Google Cloud Armor logs with Datadog
As the internet continues to evolve, cybersecurity threats—particularly Distributed Denial of Service (DDoS) attacks—are an increasingly significant concern for organizations. In this post, we’ll look at how you can use Datadog to collect Google Cloud Armor (GCA) logs and detect and respond to potential DDoS attacks in real-time. But first, we’ll briefly cover what DDoS attacks are and how they work.
What is Adaptive Security (Definition and Implementation)
Scalpers Force Barbie Collectors to Pay up to 1,200% More for Stevie Nicks Doll
Scalpers aren’t just interested in snagging the final Yeezy drops, the newest Air Jordans or tickets to see Taylor Swift on tour. They’ve also been saying “Hey, Barbie” to the latest Mattel collaboration with rock icon and Barbie enthusiast Stevie Nicks. Evidence gathered by Netacea suggests that scalper bots were involved when pre-orders for the limited-edition Stevie Nicks Barbie, unveiled by the Fleetwood Mac legend during a recent concert, sold out almost immediately.
3 Best Third-Party Risk Management Software Solutions in 2023
Fraud Prevention Tips
To prevent becoming a victim of fraud, you should always keep your data in a secure location, protect your online accounts with strong passwords and Multi-Factor Authentication (MFA), sign up for a dark web monitoring service to receive dark web alerts, learn to spot phishing scams and more. Continue reading to learn more about fraud prevention tips you should be following.
City of Huber Heights Targeted by Ransomware Attack Sunday
The City of Huber Heights is in east Ohio, north of Dayton. The suburban area has a population of around 50,000, but other populated areas are nearby. Sunday morning, November 12th, 2023, the City of Huber Heights was subject to a ransomware attack; the investigation is ongoing, as the attack disrupted many City divisions.
Digital Trust: Why SEO Poisoning is on the Rise
In the digital age, human interactions have been slowly replaced with online substitutions. We’re so used to depending on computers to perform tasks on our behalf that attackers are increasingly exploiting this trust mechanism for malicious gain. We are living in an age of unprecedented connectivity and convenience. Our daily lives are entwined with technology, from online shopping to managing our finances, to discussing key documents and answering queries in the workplace.