Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
AI-driven Analytics for IoT: Extracting Value from Data Deluge
AI-Powered MVP Development in 2024
What Are the Easy Ways to Create Online Courses?
Empowering Small Businesses Through Effective Time Tracking
Container Security: A Quick Overview
Container security is an increasingly vital aspect of modern software development and deployment. Understanding and implementing effective security measures becomes essential as organizations shift towards containerizing their applications. This article will explore practical insights and strategies for ensuring robust container security. We will delve into some best practices and tools to secure container environments, focusing on securing images and registries, container deployment, runtime security, and more.
Mitigating Risks: Effective Hybrid Cloud Security Strategies for Businesses
The Two Sides of ChatGPT: Helping MDR Detect Blind Spots While Bolstering the Phishing Threat
ChatGPT is proving to be something of a double-edged sword when it comes to cybersecurity. Threat actors employ it to craft realistic phishing emails more quickly, while white hats use large language models (LLMs) like ChatGPT to help gather intelligence, sift through logs, and more. The trouble is it takes significant know-how for a security team to use ChatGPT to good effect, while it takes just a few semi-knowledgeable hackers to craft ever more realistic phishing emails.
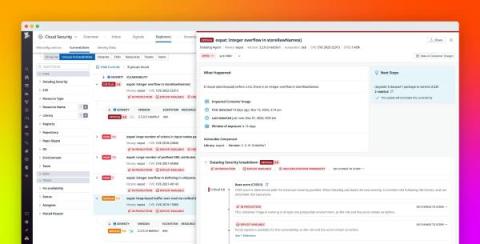
Mitigate infrastructure vulnerabilities with Datadog Cloud Security Management
Cloud environments comprise hundreds of thousands of individual components, from infrastructure-level containers and hosts to access-level user and cloud accounts. With this level of complexity, continuous and end-to-end visibility into your environment is vital for detecting, prioritizing, and fixing vulnerabilities before attackers can take advantage of them.
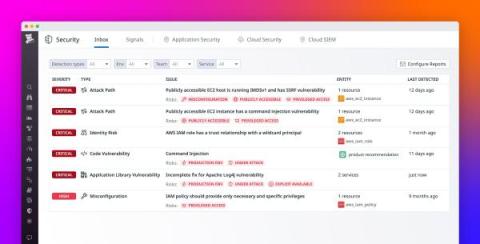
Easily identify and prioritize your top security risks with Datadog Security Inbox
In today’s complex cloud environments, security and engineering teams need to manage vulnerabilities and misconfigurations across multiple layers of the stack, including cloud resources, clusters, containers, and applications. Often, this results in a lengthy list of problems that lacks prioritization and is daunting for users to address.