Finding CVE-2022-22954 with Zeek
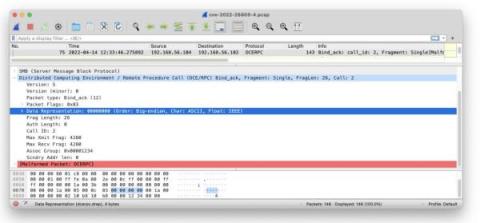
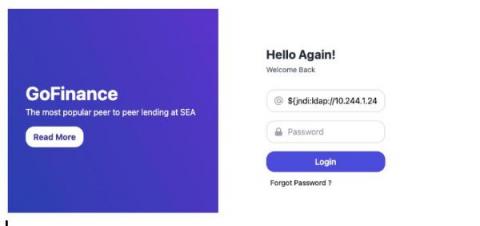
CISA released a warning to federal agencies on May 18 that APT actors are actively exploiting recent vulnerabilities found in VMware, including CVE-2022-22954. Your first thought may have been to want new signatures, indicators, and/or behavioral techniques to detect attempted and successful exploits. If you’re a Zeek user or Corelight customer, you’ll find that sometimes you’re already getting what you need.