Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
A Quick Guide To Information Security Programs
Broadly speaking, an information security program is a set of activities and initiatives that support a company’s information technology while protecting the security of business data and enabling the company to accomplish its business objectives. An information security program safeguards the proprietary information of the business and its customers. The Gramm-Leach-Bliley Act (GLBA) has a more specific definition of what a security information program should entail.
GitHub Supply Chain Attacks Highlight the Urgency of Zero Trust SaaS Data Security
In early April, the tech industry witnessed a major GitHub security incident targeting GitHub organizations using Heroku and Travis CI. GitHub was made aware of this threat via an attack leveraging AWS API keys to GitHub’s own npm production infrastructure. As upstream security risks within SaaS platforms become more common, organizations that leverage these platforms are relying on tools like Nightfall to protect themselves.
Understanding the GLBA Safeguards Rule
The Gramm-Leach-Bliley Act (GLBA) aims to protect consumer financial privacy with three provisions: the Financial Privacy Rule, the Safeguards Rule, and the Pretexting Provisions. In our previous post, we covered the GLBA Financial Privacy Rule and what financial institutions, as defined by the GLBA, need to know to be compliant.
5 Key Considerations for Microsoft Teams Security
Microsoft Teams is a fantastic collaboration tool allowing people to share data effortlessly within the same organization and even across organizations. Unfortunately, because it was built with collaboration as the primary driver, it can be easy to ‘overshare’ data you don’t want to share.
Nightfall Joins Snyk Partner Program to Expand Security across the SDLC
We’re pleased to announce that Nightfall has joined Snyk’s Technology Alliance Partner Program (TAPP). Nightfall will sit alongside partners like RedHat, and Hashicorp to provide critical DevSecOps functionality to developers.
Technical Spotlight: How to Protect and Watermark CAD Files
While the data breaches that make the headlines often focus on personal data, there’s a lot more at stake if a hacker cracks open the gates. There’s even higher stakes when intellectual property (IP) theft is the goal potentially stripping away an organization’s competitive advantage. It’s not just hackers that are a threat to IP. Employees, contractors and partners all pose a risk to IP from accidental or deliberate data loss.
Best practices for reducing sensitive data blindspots and risk
Modern applications log vast amounts of personal and business information that should not be accessible to external sources. Organizations face the difficult task of securing and storing this sensitive data in order to protect their customers and remain compliant. But there is often a lack of visibility into the sensitive data that application services are logging, especially in large-scale environments, and the requirements for handling it can vary across industries and regions.
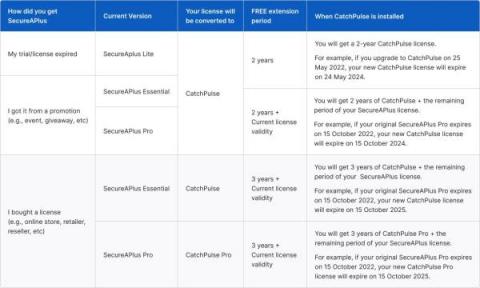
SecureAPlus users upgrade FREE to CatchPulse
SecureAge Technology recently announced the relaunch and renaming of SecureAPlus which is taking place in May 2022. The new upgraded version is now known as CatchPulse. In this post, we would like to share with our existing home customers how this change will affect your SecureAPlus Essentials and Pro installations.