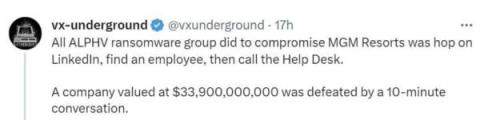
MGM Suffers Ransomware Attack that Started with a Simple Helpdesk Call
As the aftermath unfolds, the details around the recent attack on MGM Resorts, providing crucial insight into the attacks impact, who’s responsible, and how it started. On September 11, Las Vegas-based MGM Resorts International reported a cybersecurity “issue” affecting many of the company’s systems.