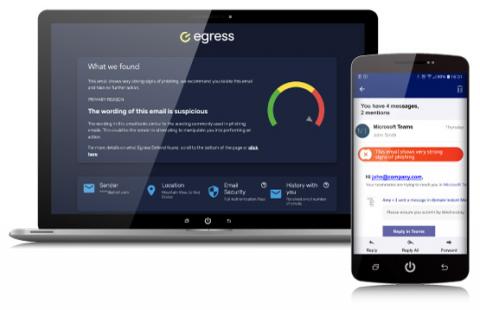
Graymail and its impact on cybersecurity
Graymail – technically, it’s not bad, but it’s not necessarily good, either. This type of email falls in between. At best it’s useful, usually it’s an annoyance, and at worst, it’s a potential cybersecurity threat. The accepted definition for graymail is emails that aren’t spam or phishing, but which the recipient may perceive as inbox clutter.