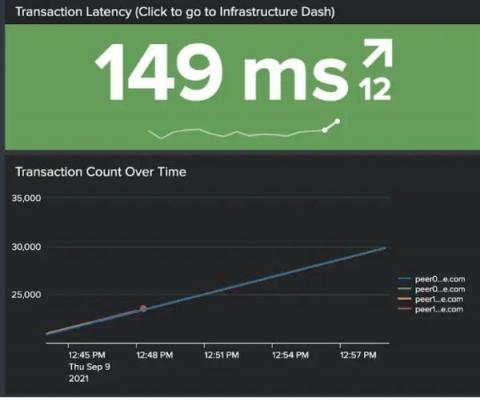
Listen To Those Pipes: Part 2
This blog post is part thirty of the "Hunting with Splunk: The Basics" series. Shannon Davis provided the first half of this blog on pipe hunting in part twenty-nine, and will now run through the second half! – Ryan Kovar