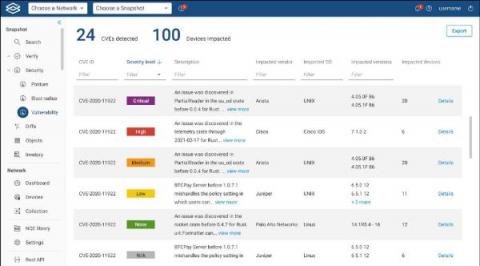
Let There Be Visibility: See Your Entire Cloud Estate in a Single, Normalized View
Do cloud environments really have to be so foggy? Absolutely not. Yet, many enterprises have come to accept that not having full visibility into their cloud estate is just “how it is.”