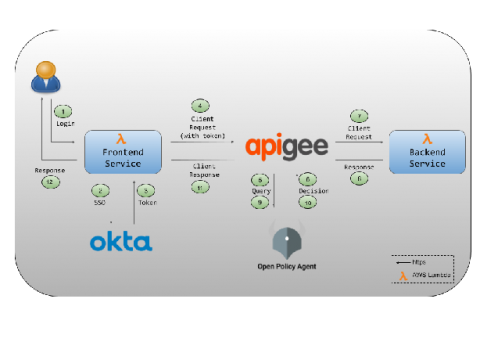
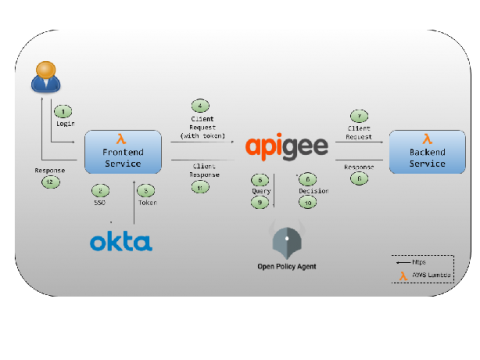
API Authorization at the Gateway with Apigee, Okta, and OPA (Part 2)
This is the second post in a two-part series about enforcing API authorization policies using Apigee, Okta and OPA. While the first post explained how to set up all three to work together, this post dives into detail on the policies that go along with the working code. The application we will be discussing is based on a hypothetical medical insurance provider Acme Health Care.