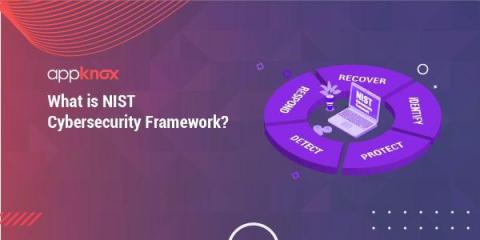
5 Things to Do Immediately After Your Startup Is the Victim of a Cyber Attack
Stats suggest that 43% of cyber attacks target small businesses and 60% of these attacks are encountered within the first 6 months of setting up a business. While the horrors of cyber attacks are known to everyone, getting such a fatal blow right when you are starting, can send your startup on a trip to Bermuda Triangle! However, proper planning and having a reliable security strategy can help you bring back from the place of no return!